本文檔介紹Firepower的配置和驗證,以及安全防火牆內部交換機捕獲。
This document presents the configuration and validation of Firepower, as well as the capture of the internal switchboard of the security firewall.
基本的產品知識,捕獲分析。
Basic product knowledge, capture analysis.
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
The information in this paper is based on the devices in a given laboratory environment. All devices used in the text are activated from the cleared (predicted) configuration. If you are working on your network, make sure you understand the implications of any instructions.
本文中的資訊係根據以下軟體和硬體版本:
The information in this paper is based on the following software and hard version:
- 安全防火牆31xx、42xx
- Firepower 41xx
- Firepower 93xx
- Cisco安全可擴充作業系統(FXOS) 2.12.0.x
- 思科安全防火牆威脅防禦(FTD) 7.2.0.x、7.4.1-172
- 思科安全防火牆管理中心(FMC) 7.2.0.x、7.4.1-172
- 調適型安全裝置(ASA) 9.18(1)x、9.20(x)
- Wireshark 3.6.7 (https://www.wireshark.org/download.html)
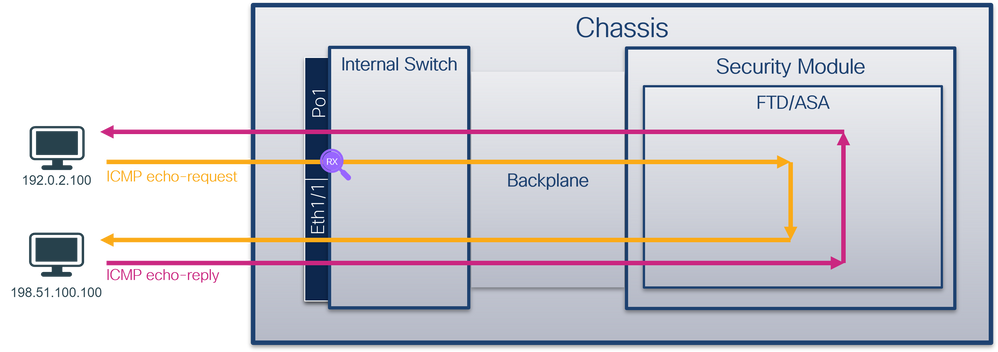
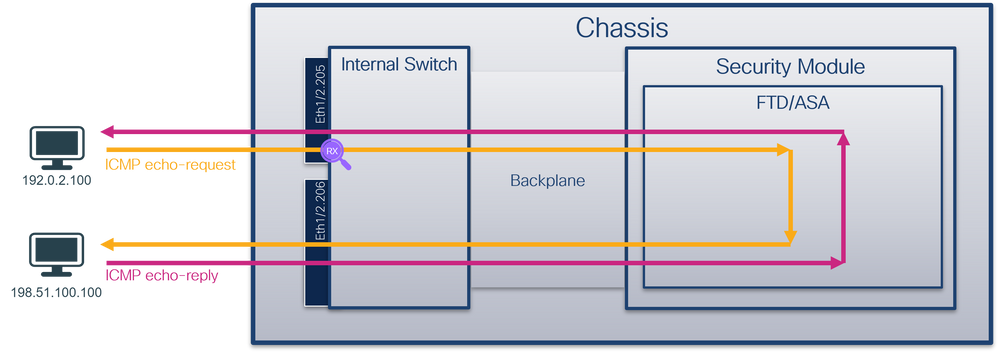
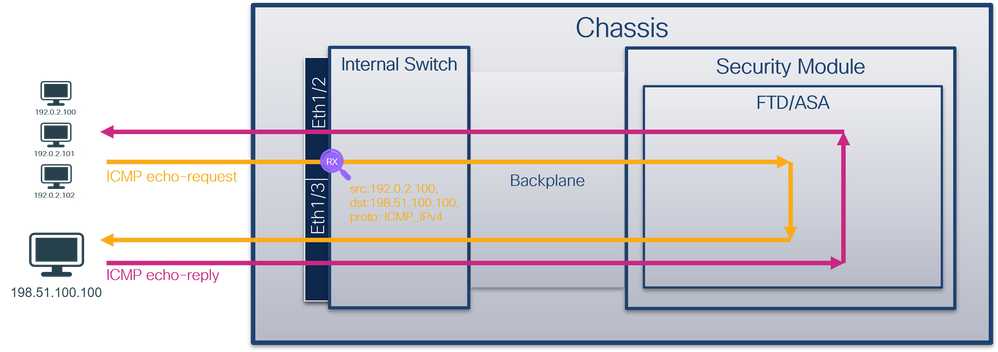
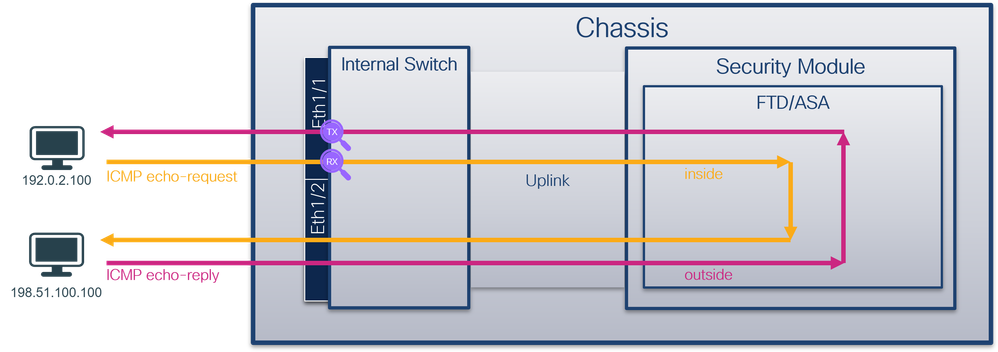
從資料包流的角度來看,Firepower 4100/9300和安全防火牆3100/4200的體系結構視覺化,如下圖所示:
From the point of view of the data stream, Firepower 4100/9300 and the security firewall 3100/4200 have a visualization of the structure of the system, as shown in the following graph:
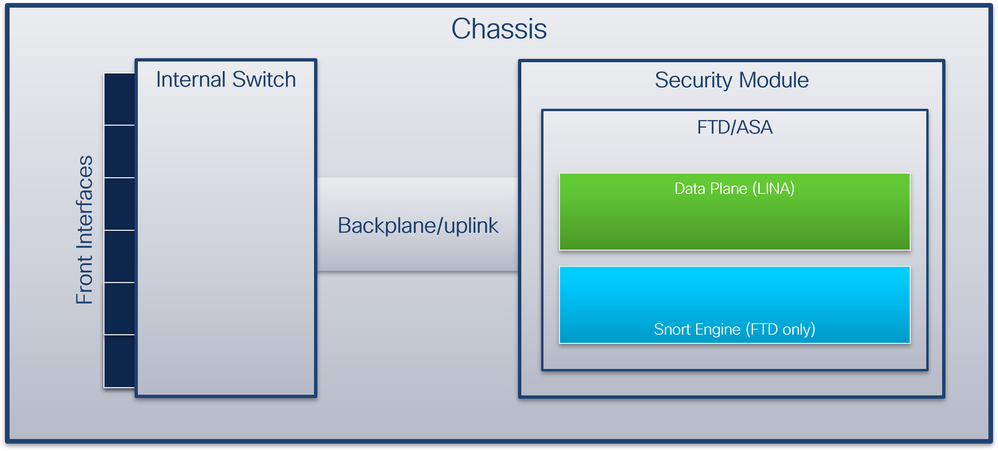

機箱包括以下元件:
The boxes include the following components:
- 內部交換機 -將資料包從網路轉發到應用,反之亦然。內部交換機連線到位於內建介面模組或外部網路模組上的前介面,並連線到外部裝置,例如交換機。前端介面的示例包括Ethernet 1/1、Ethernet 2/4等。「前線」並不是一個強有力的技術定義。在本文檔中,它用於區分連線到外部裝置的介面與背板或上行鏈路介面。
- 背板或上行鏈路 -將安全模組(SM)連線到內部交換機的內部介面。
- 管理上行鏈路 -安全防火牆3100/4200專用的內部介面,提供內部交換機和應用程式之間的管理流量路徑。
下表顯示Firepower 4100/9300上的背板介面和安全防火牆3100/4200上的上行鏈路介面:
The following table shows the backboard interface on Firepower 4100/9300 and the uplink interface on the security firewall 3100/4200:
| 平台 |
支援的安全模組數目 Number of security modules supported by |
背板/上行鏈路介面 |
管理上行鏈路介面 manages the uplink interface |
對映的應用介面 The application interface for |
| Firepower 4100(Firepower 4110/4112除外) Firepower 4100 (except Firepower 4110/4112) |
1 |
SM1: Ethernet1/9 Ethernet1/10 |
不適用 Not suitable. |
Internal-Data0/0 Internal-Data0/1 |
| Firepower 4110/4112 |
1 |
Ethernet1/9 |
不適用 Not suitable. |
Internal-Data0/0 |
| Firepower 9300 |
3 |
SM1: Ethernet1/9 Ethernet1/10 SM2: Ethernet1/11 Ethernet1/12 SM3: Ethernet1/13 Ethernet1/14 |
不適用 Not suitable. |
Internal-Data0/0 Internal-Data0/1
Internal-Data0/1
Internal-Data0/1 |
| 安全防火牆3100 Security firewall 3100 |
1 |
SM1:in_data_uplink1 |
in_mgmt_uplink1 |
Internal-Data0/1 管理1/1 |
| 安全防火牆4200 Security firewall 4200 |
1 |
SM1:in_data_uplink1 SM1:in_data_uplink2(僅限4245) SM1:in_data_uplink (4245) |
in_mgmt_uplink1 in_mgmt_uplink2 |
Internal-Data0/1 Internal-Data0/2(僅限4245) International-Data0/2 (4245) br> 管理1/1 管理1/2 |
在每模組具有2個背板介面的Firepower 4100/9300或具有2個資料上行鏈路介面的安全防火牆4245中,內部交換機和模組上的應用程式在兩個介面上執行流量負載均衡。
In Firewall 4245 with two backboard interfaces for each module, Firepower 4100/9300 or two data uplink interfaces, applications on internal switches and modules run traffic load balances on two interfaces.
- 安全模組、安全引擎或刀片 -安裝FTD或ASA等應用程式的模組。Firepower 9300最多支援3個安全模組。
- 對映的應用介面 -應用(如FTD或ASA)中的背板或上行鏈路介面的名稱。
使用show interface detail命令驗證內部介面:
Using show interface detail command to verify internal interfaces:
> show interface detail | grep Interface
Interface Internal-Control0/0 "ha_ctl_nlp_int_tap", is up, line protocol is up
Control Point Interface States:
Interface number is 6
Interface config status is active
Interface state is active
Interface Internal-Data0/0 "", is up, line protocol is up
Control Point Interface States:
Interface number is 2
Interface config status is active
Interface state is active
Interface Internal-Data0/1 "", is up, line protocol is up
Control Point Interface States:
Interface number is 3
Interface config status is active
Interface state is active
Interface Internal-Data0/2 "nlp_int_tap", is up, line protocol is up
Control Point Interface States:
Interface number is 4
Interface config status is active
Interface state is active
Interface Internal-Data0/3 "ccl_ha_nlp_int_tap", is up, line protocol is up
Control Point Interface States:
Interface number is 5
Interface config status is active
Interface state is active
Interface Internal-Data0/4 "cmi_mgmt_int_tap", is up, line protocol is up
Control Point Interface States:
Interface number is 7
Interface config status is active
Interface state is active
Interface Port-channel6.666 "", is up, line protocol is up
Interface Ethernet1/1 "diagnostic", is up, line protocol is up
Control Point Interface States:
Interface number is 8
Interface config status is active
Interface state is active
Firepower 4100/9300
為做出轉發決策,內部交換機使用介面VLAN標籤或埠VLAN標籤以及虛擬網路標籤(VN標籤)。
For decision-making purposes, the internal switchboard uses VLAN tags or port VLAN tags and virtual network tags (VN tags) .
內部交換機使用埠VLAN標籤來標識介面。交換機會將埠VLAN標籤插入到位於前介面的每個入口資料包中。VLAN標籤由系統自動配置,無法手動更改。 標籤值可以在fxos命令shell中檢查:
The internal switcher uses the port VLAN tag to mark the interface. The exchange opportunity inserts the port VLAN tag in each entry package in the front. The VLAN tag is automatically configured by the system and cannot be changed manually. & nbsp; tag values can be checked in fxos command shell:
firepower# connect fxos
…
firepower(fxos)# show run int e1/2
!Command: show running-config interface Ethernet1/2
!Time: Tue Jul 12 22:32:11 2022
version 5.0(3)N2(4.120)
interface Ethernet1/2
description U: Uplink
no lldp transmit
no lldp receive
no cdp enable
switchport mode dot1q-tunnel
switchport trunk native vlan 102
speed 1000
duplex full
udld disable
no shutdown
VN標籤也由內部交換機插入,用於轉發資料包到應用。系統會自動設定它,且無法手動變更。
The VN tag is also inserted by the internal switcher and is used to convert the package to the application. The system automatically sets it and cannot change it manually.
埠VLAN標籤和VN標籤與應用共用。應用程式將各自的輸出介面VLAN標籤和VN標籤插入每個封包中。當背板介面上的內部交換機接收到來自應用的資料包時,交換機讀取出口介面VLAN標籤和VN標籤,辨識應用和出口介面,刪除埠VLAN標籤和VN標籤,並將資料包轉發到網路。
The port VLAN tags and VN tags are shared with applications. The application inserts the respective output interface VLAN tags and VN tags into each package. When the internal switcher on the backboard receives the data package from the application, the switcher reads the export interface VLAN tags and VN tags, identifies applications and export interfaces, deletes the port VLAN tags and VN tags, and forwards the package to the web.
安全防火牆3100/4200
security firewall 3100/4200
與Firepower 4100/9300一樣,內部交換機使用埠VLAN標籤來辨識介面。
Like Firepower 4100/9300, the internal switchboard uses the port VLAN tag to identify the interface.
埠VLAN標籤與應用程式共用。應用程式將各個輸出介面VLAN標籤插入每個封包中。當上行鏈路介面上的內部交換機接收到來自應用的資料包時,交換機讀取出口介面VLAN標籤,辨識出口介面,刪除埠VLAN標籤,並將資料包轉發到網路。
The port VLAN tags are shared with the application. The application inserts each output interface VLAN tag into each package. When the internal switcher on the uplink interface receives the data package from the application, the switchboard reads the export interface VLAN tags, identifies the export interface, deletes the port VLAN tags and forwards the data package to the network.
Firepower 4100/9300和安全防火牆3100
Firepower 4100/9300和安全防火牆3100防火牆支援內部交換機介面上的資料包捕獲。
Firepower 4100/9300 and the security firewall 3100 supported the capture of the data package on the internal switchboard interface.
下圖顯示了機箱和應用中資料包路徑上的資料包捕獲點:
The following graph shows the data pack capture point on the engine and application active data package path:
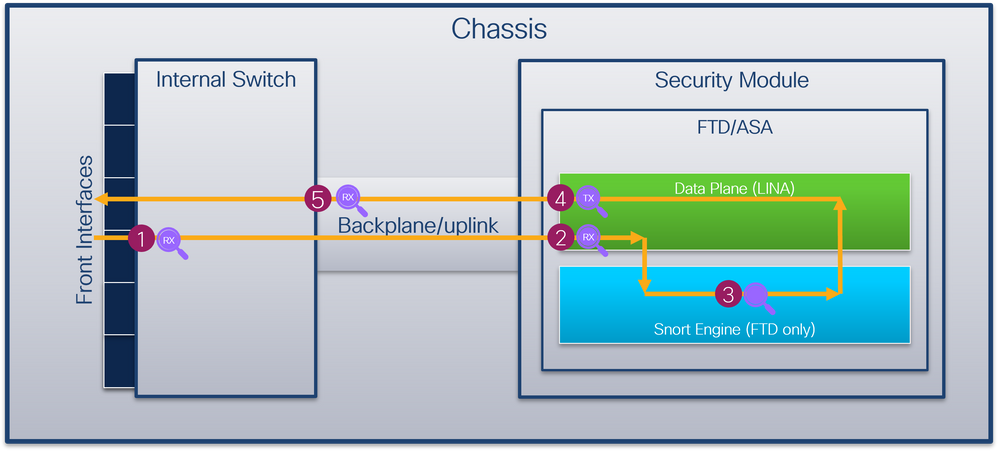
捕獲點包括:
The capture points include:
- 內部交換機前介面入口捕獲點。前端介面是連線到對等裝置(如交換機)的任何介面。
- 資料平面介面入口捕獲點
- Snort捕獲點
- 資料平面介面出口捕獲點
- 內部交換機背板或上行鏈路入口捕獲點。背板或上行鏈路介面將內部交換機連線到應用。
內部交換器僅支援輸入介面擷取。也就是說,只能捕獲從網路或ASA/FTD應用接收的資料包。不支援輸出封包擷取。
The internal switcher only supports the input interface. That is, only the data package received from the Internet or from the ASA/FTD application can be captured. does not support the output of the package.
安全防火牆4200
security firewall 4200 >/strang
安全防火牆4200防火牆支援內部交換機介面上的資料包捕獲。下圖顯示了機箱和應用中資料包路徑上的資料包捕獲點:
The security firewall 4200 supports the capture of the data package on the internal switchboard interface.
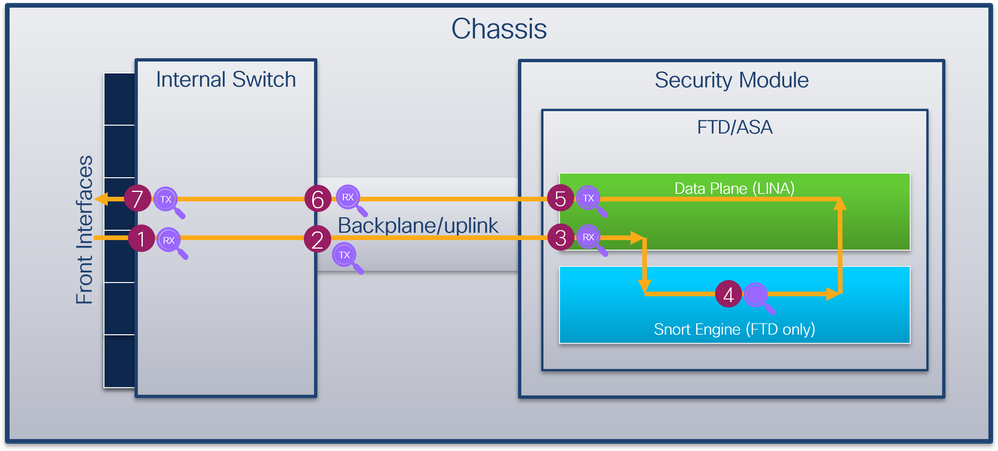
捕獲點包括:
The capture points include:
- 內部交換機前介面入口捕獲點。前端介面是連線到對等裝置(如交換機)的任何介面。
- 內部交換機背板介面出口捕獲點。
- 資料平面介面入口捕獲點
- Snort捕獲點
- 資料平面介面出口捕獲點
- 內部交換機背板或上行鏈路入口捕獲點。背板或上行鏈路介面將內部交換機連線到應用。
- 內部交換機前介面出口捕獲點。
內部交換機可選擇支援雙向-入口和出口-捕獲。預設情況下,內部交換器會擷取輸入方向上的封包。
The inside switcher selects to support two-way - entrance and exit - capture.
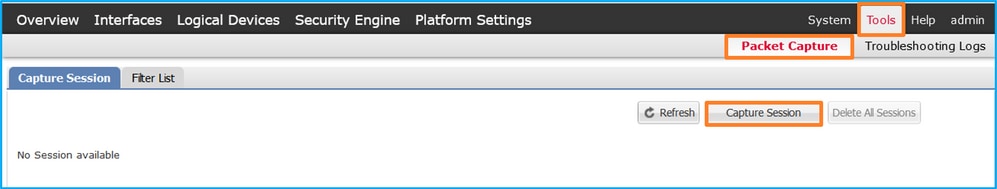
可以在FCM上的Tools > Packet Capture中或在FXOS CLI中的scope packet-capture中配置Firepower 4100/9300內部交換機捕獲。有關資料包捕獲選項的說明,請參閱Cisco Firepower 4100/9300 FXOS機箱管理器配置指南或Cisco Firepower 4100/9300 FXOS CLI配置指南的故障排除一章資料包捕獲部分。
An internal switcher of Firepower 4100/9300 may be located on FCM
這些場景包括Firepower 4100/9300內部交換機捕獲的常見使用案例。
These scenes include common usage cases captured by Firepower 4100/9300 internal switchboards.
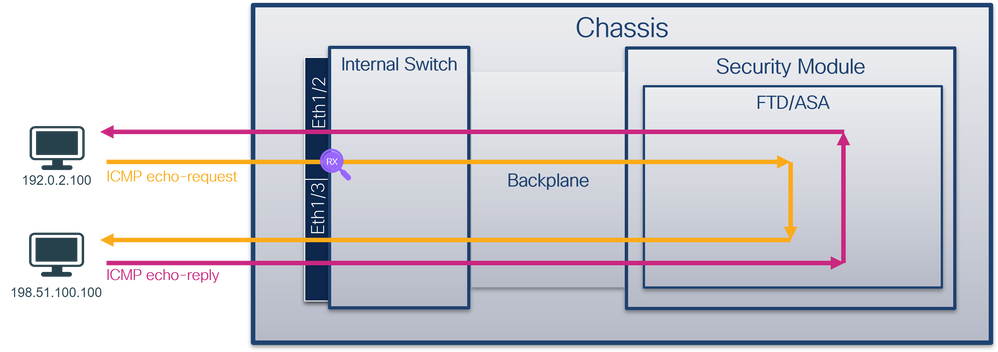
使用FCM和CLI在介面Ethernet1/2或Portchannel1介面上配置和驗證資料包捕獲。對於埠通道介面,請確保選擇所有物理成員介面。
Use FCM and CLI to configure and authenticate the data packs on interface 1/2 or Portchannel 1. For port interfaces, make sure that all physical interfaces are selected.
拓撲、資料包流和捕獲點
pings, data packs, catch points
組態
FCM
按照FCM上的以下步驟在介面Ethernet1/2或Portchannel1上配置資料包捕獲:
The following steps on the FCM have been taken to configure the data packs on the interface 1/2 or Portchannel1:
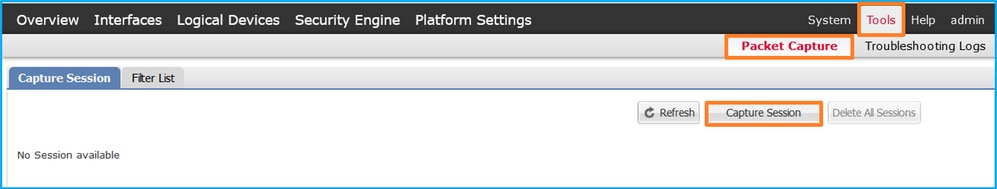
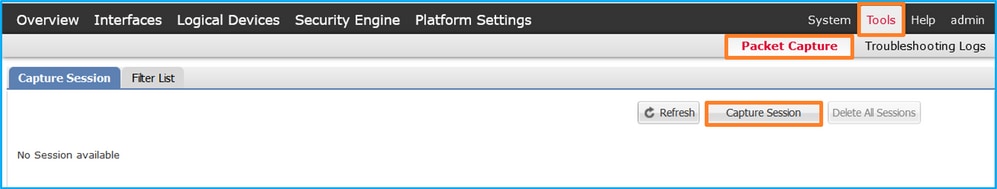
- 使用Tools > Packet Capture > Capture Session建立新的捕獲會話:
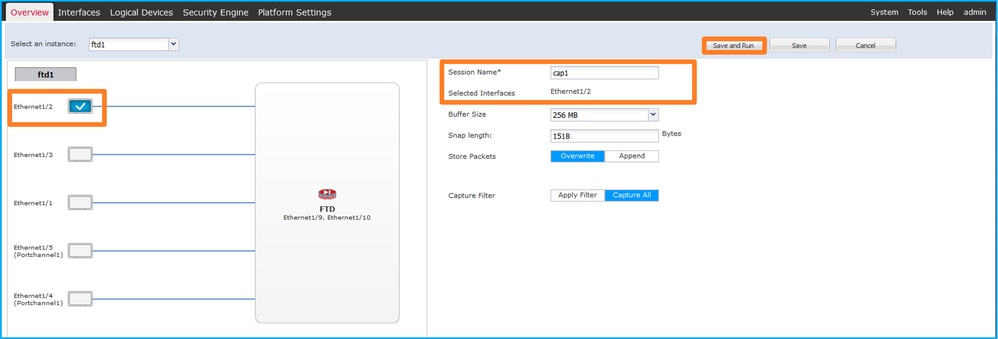
- 選擇介面Ethernet1/2,提供會話名稱,然後按一下Save and Run啟用捕獲:
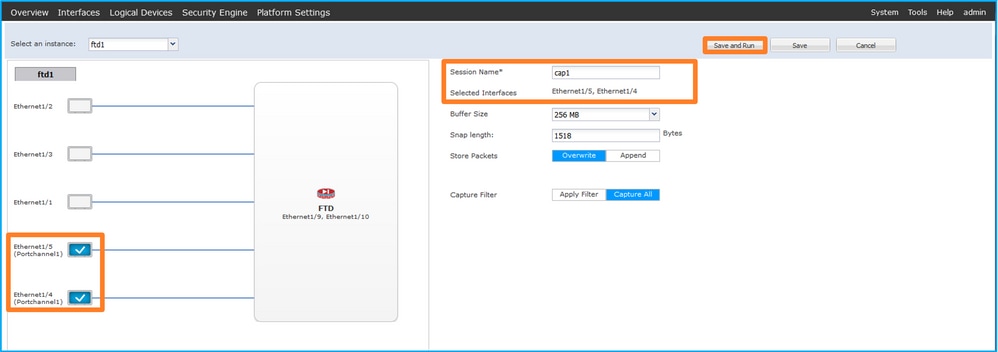
- 對於埠通道介面,請選擇所有物理成員介面,提供會話名稱並按一下Save and Run以啟用捕獲:
FXOS CLI
按照FXOS CLI上的以下步驟在介面Ethernet1/2或Portchannel1上配置資料包捕獲:
The following steps on FXOS CLI were taken to configure the data packs on interface 1/2 Ethernet or Portchannel1:
- 辨識應用程式型別和辨識碼:
firepower# scope ssa
firepower /ssa # show app-instance
App Name Identifier Slot ID Admin State Oper State Running Version Startup Version Deploy Type Turbo Mode Profile Name Cluster State Cluster Role
---------- ---------- ---------- ----------- ---------------- --------------- --------------- ----------- ---------- ------------ --------------- ------------
ftd ftd1 1 Enabled Online 7.2.0.82 7.2.0.82 Native No Not Applicable None
- 對於埠通道介面,請確定其成員介面:
firepower# connect fxos
<output skipped>
firepower(fxos)# show port-channel summary
Flags: D - Down P - Up in port-channel (members)
I - Individual H - Hot-standby (LACP only)
s - Suspended r - Module-removed
S - Switched R - Routed
U - Up (port-channel)
M - Not in use. Min-links not met
--------------------------------------------------------------------------------
Group Port- Type Protocol Member Ports
Channel
--------------------------------------------------------------------------------
1 Po1(SU) Eth LACP Eth1/4(P) Eth1/5(P)
- 建立擷取階段作業:
firepower# scope packet-capture
firepower /packet-capture # create session cap1
firepower /packet-capture/session* # create phy-port Eth1/2
firepower /packet-capture/session/phy-port* # set app ftd
firepower /packet-capture/session/phy-port* # set app-identifier ftd1
firepower /packet-capture/session/phy-port* # up
firepower /packet-capture/session* # enable
firepower /packet-capture/session* # commit
firepower /packet-capture/session #
對於埠通道介面,為每個成員介面配置單獨的捕獲:
For port channel interfaces, separate captures are provided for each member interface:
firepower# scope packet-capture
firepower /packet-capture # create session cap1
firepower /packet-capture/session* # create phy-port Eth1/4
firepower /packet-capture/session/phy-port* # set app ftd
firepower /packet-capture/session/phy-port* # set app-identifier ftd1
firepower /packet-capture/session/phy-port* # up
firepower /packet-capture/session* # create phy-port Eth1/5
firepower /packet-capture/session/phy-port* # set app ftd
firepower /packet-capture/session/phy-port* # set app-identifier ftd1
firepower /packet-capture/session/phy-port* # up
firepower /packet-capture/session* # enable
firepower /packet-capture/session* # commit
firepower /packet-capture/session #
驗證
Verify/strong>
FCM
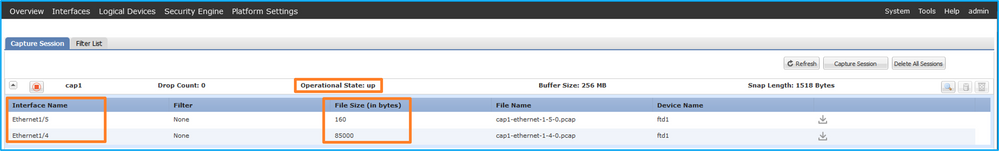
驗證介面名稱,確保Operational Status為up且File Size (in bytes)增加:
Validation of the interface

Portchannel1與成員介面Ethernet1/4和Ethernet1/5:
Portchannel1 and member interface Ethernet1/4 and Ethernet1/5:
FXOS CLI
驗證scope packet-capture中的捕獲詳細資訊:
More detailed information on the capture in copet-capture:
firepower# scope packet-capture
firepower /packet-capture # show session cap1
Traffic Monitoring Session:
Packet Capture Session Name: cap1
Session: 1
Admin State: Enabled
Oper State: Up
Oper State Reason: Active
Config Success: Yes
Config Fail Reason:
Append Flag: Overwrite
Session Mem Usage: 256 MB
Session Pcap Snap Len: 1518 Bytes
Error Code: 0
Drop Count: 0
Physical ports involved in Packet Capture:
Slot Id: 1
Port Id: 2
Pcapfile: /workspace/packet-capture/session-1/cap1-ethernet-1-2-0.pcap
Pcapsize: 75136 bytes
Filter:
Sub Interface: 0
Application Instance Identifier: ftd1
Application Name: ftd
具有成員介面Ethernet1/4和Ethernet1/5的Port-channel 1:
Port-channel with membership 1/4 and Ethernet 1/5:
firepower# scope packet-capture
firepower /packet-capture # show session cap1
Traffic Monitoring Session:
Packet Capture Session Name: cap1
Session: 1
Admin State: Enabled
Oper State: Up
Oper State Reason: Active
Config Success: Yes
Config Fail Reason:
Append Flag: Overwrite
Session Mem Usage: 256 MB
Session Pcap Snap Len: 1518 Bytes
Error Code: 0
Drop Count: 0
Physical ports involved in Packet Capture:
Slot Id: 1
Port Id: 4
Pcapfile: /workspace/packet-capture/session-1/cap1-ethernet-1-4-0.pcap
Pcapsize: 310276 bytes
Filter:
Sub Interface: 0
Application Instance Identifier: ftd1
Application Name: ftd
Slot Id: 1
Port Id: 5
Pcapfile: /workspace/packet-capture/session-1/cap1-ethernet-1-5-0.pcap
Pcapsize: 160 bytes
Filter:
Sub Interface: 0
Application Instance Identifier: ftd1
Application Name: ftd
收集捕獲檔案
collects capture files
按照收集Firepower 4100/9300內部交換機捕獲檔案部分中的步驟操作。
Collecter of Firepower 4100/9300 internal switchboards in accordance with
捕獲檔案分析
capture file analysis
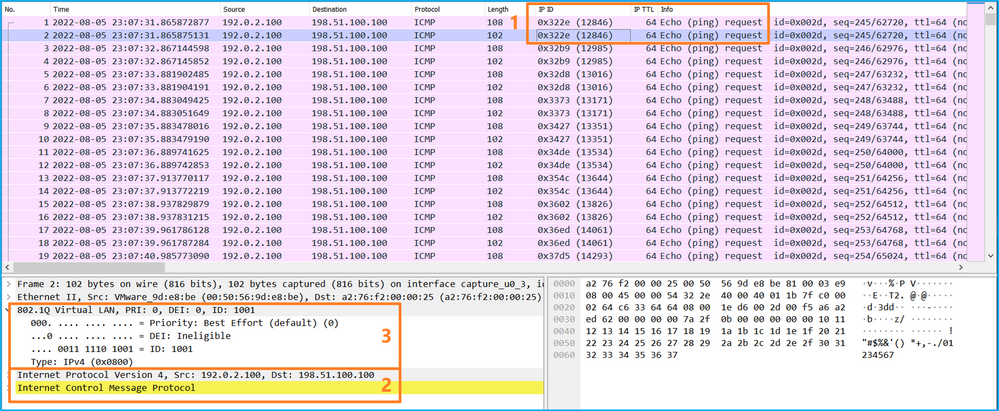
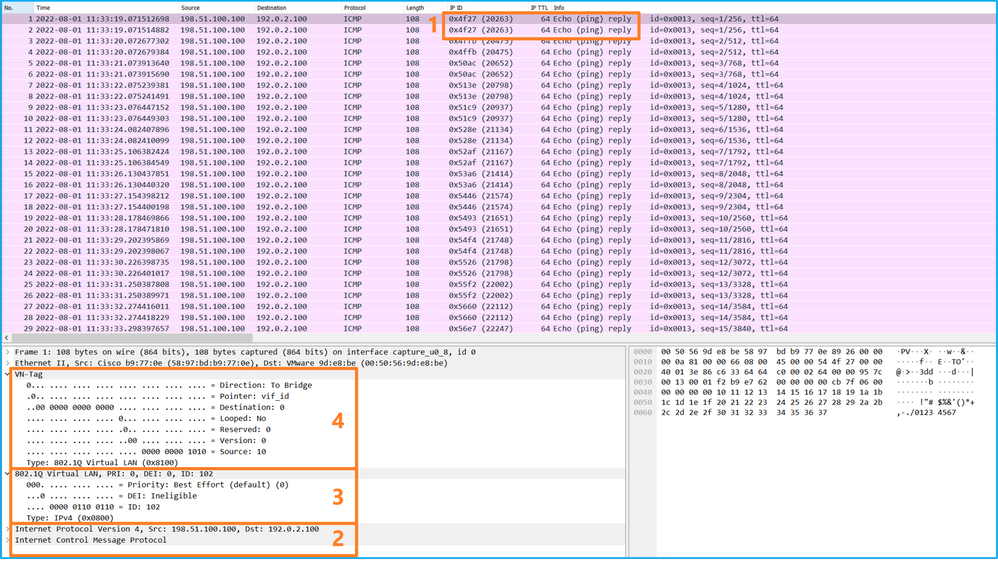
使用資料包捕獲檔案讀取器應用程式打開Ethernet1/2的捕獲檔案。選擇第一個資料包並檢查要點:
Opens the Ethernet1/2 capture file using the data pack to capture the file reader application. Select the first package and check the point:
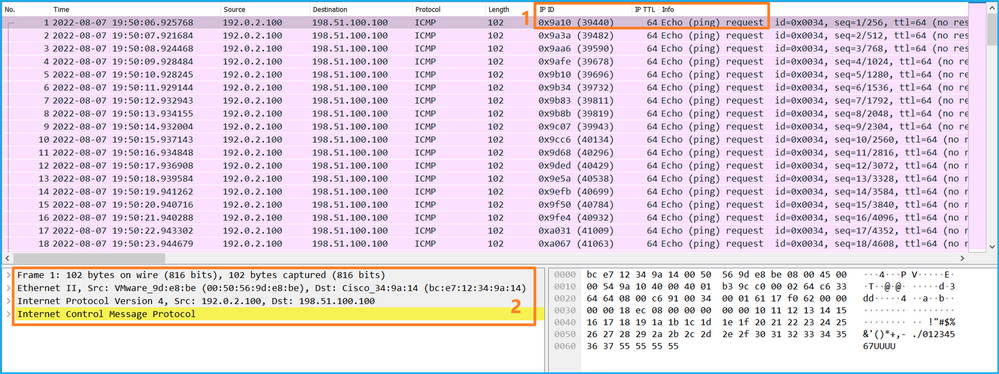
- 僅捕獲ICMP回應請求資料包。捕獲每個資料包並顯示2次。
- 原始資料包報頭沒有VLAN標籤。
- 內部交換機插入用於辨識輸入介面Ethernet1/2的其他埠VLAN標籤102。
- 內部開關插入一個附加VN標籤。
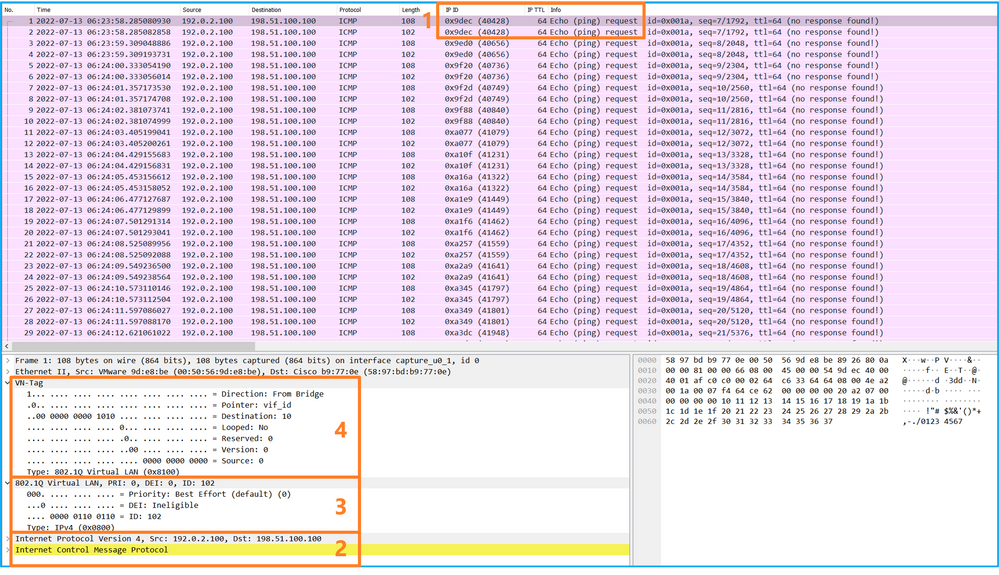
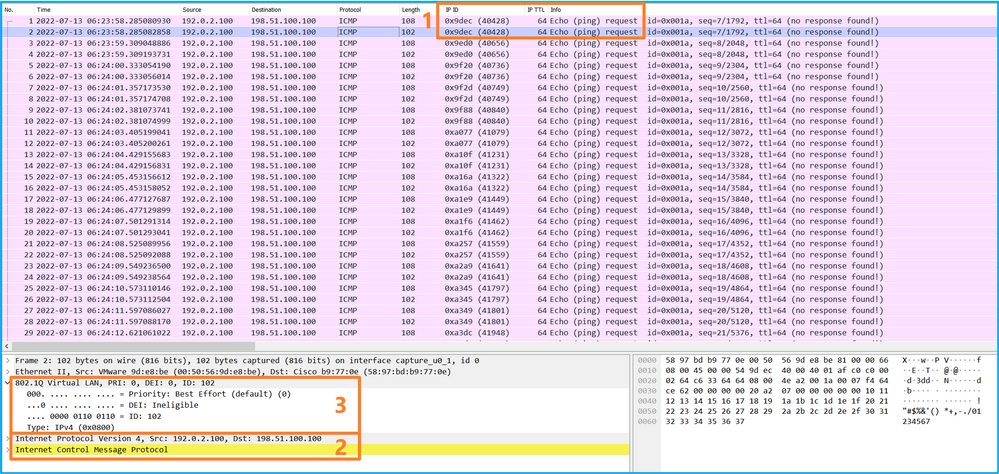
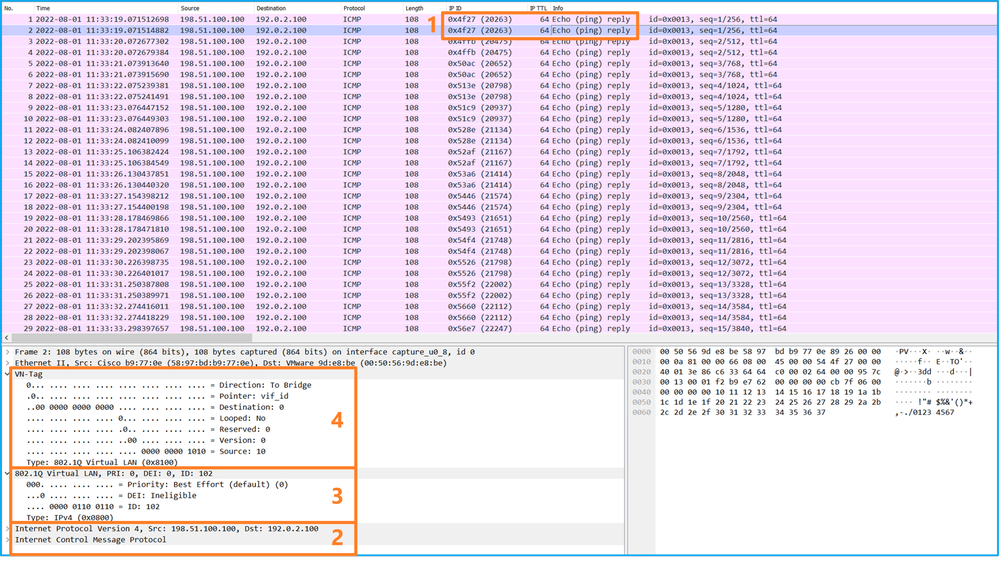
選擇第二個資料包並檢查要點:
Select the second package and check the point:
- 僅捕獲ICMP回應請求資料包。捕獲每個資料包並顯示2次。
- 原始資料包報頭沒有VLAN標籤。
- 內部交換機插入用於辨識輸入介面Ethernet1/2的其他埠VLAN標籤102。
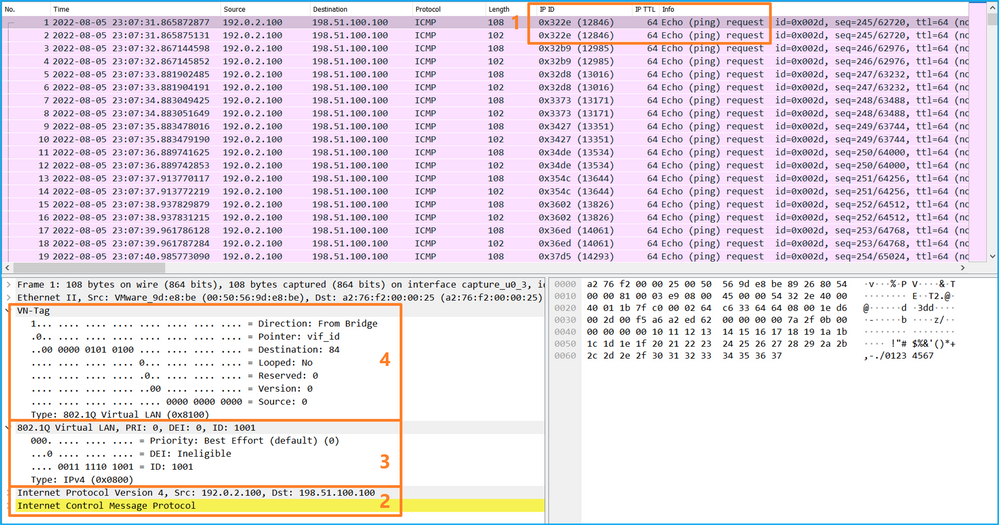
打開Portchannel1成員介面的捕獲檔案。選擇第一個資料包並檢查要點:
Opens the capture file of the Portchannel1 interface. Select the first package and check the point:
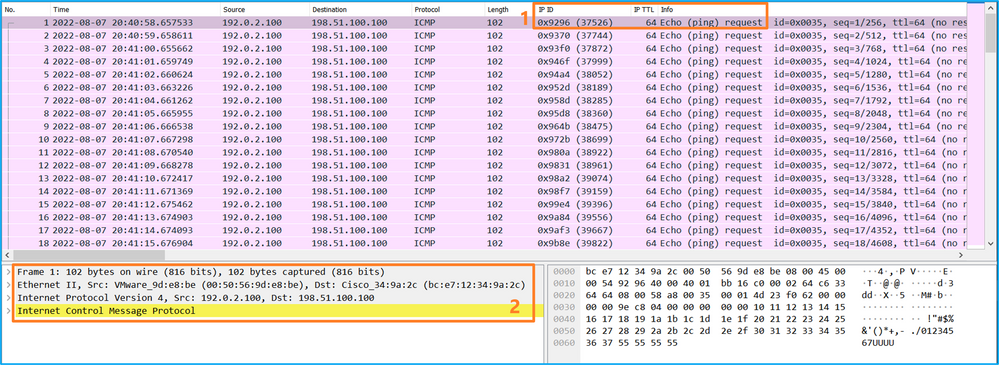
- 僅捕獲ICMP回應請求資料包。捕獲每個資料包並顯示2次。
- 原始資料包報頭沒有VLAN標籤。
- 內部交換機插入一個額外的埠VLAN標籤1001,用於辨識輸入介面Portchannel1。
- 內部開關插入一個附加VN標籤。
選擇第二個資料包並檢查要點:
Select the second package and check the point:
- 僅捕獲ICMP回應請求資料包。捕獲每個資料包並顯示2次。
- 原始資料包報頭沒有VLAN標籤。
- 內部交換機插入一個額外的埠VLAN標籤1001,用於辨識輸入介面Portchannel1。
說明
Help
在前端介面上設定封包擷取時,交換器會同時擷取每個封包兩次:
When you set a package on the front interface, the switch will take each package twice at the same time:
- 在插入埠VLAN標籤之後。
- 在插入VN標籤之後。
按照操作順序,VN標籤在比埠VLAN標籤插入更晚的階段插入。但是,在捕獲檔案中,帶有VN標籤的資料包比帶有埠VLAN標籤的資料包顯示得更早。
In the operating order, the VN tag is inserted at a later stage than the port VLAN tag. However, in the capture file, the bag with the VN tag is shown earlier than the bag with the port VLAN tag.
此表格總結列出作業:
The summary of this table lists the homework:
| 工作 |
捕獲點 |
捕獲的資料包中的內部埠VLAN The inside port of the |
方向 |
捕獲的流量 captured traffic |
| 在介面Ethernet1/2上配置並檢驗資料包捕獲 Configure and verify data pack capture on interface Ethernet1/2 |
Ethernet1/2 |
102 |
僅限入口 Access only |
從主機192.0.2.100到主機198.51.100.100的ICMP回應請求 From host 192.02.100 to host 198.51.10.100 ICMP response |
| 在介面Portchannel1上配置並檢驗帶有成員介面Ethernet1/4和Ethernet1/5的資料包捕獲 Configure and test data packs on interface Portchannel1 with user interfaces Ethernet1/4 and Ethernet1/5 |
Ethernet1/4 Ethernet1/5 |
1001 |
僅限入口 Access only |
從主機192.0.2.100到主機198.51.100.100的ICMP回應請求 From host 192.02.100 to host 198.51.10.100 ICMP response |
使用FCM和CLI配置並驗證背板介面上的資料包捕獲。
Use FCM and CLI to configure and verify data pack captures on backboard interfaces.
拓撲、資料包流和捕獲點
pings, data packs, catch points
組態
FCM
按照FCM上的以下步驟在背板介面上配置資料包捕獲:
Configure the data pack on the backboard interface according to the following steps on the FCM:
- 使用Tools > Packet Capture > Capture Session建立新的捕獲會話:
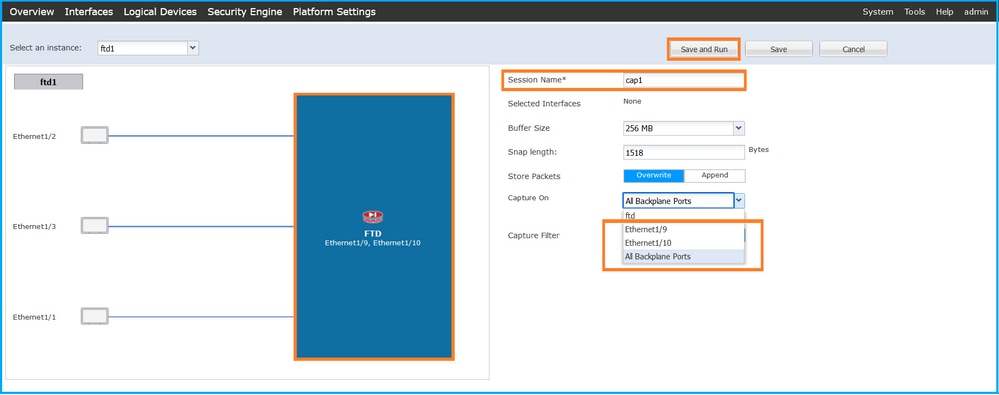
- 要捕獲所有背板介面上的資料包,請從下拉選單中選擇Capture On和All Backplane Ports。或者,選擇特定的背板介面。在這種情況下,可以使用背板介面Ethernet1/9和Ethernet1/10。提供會話名稱,然後按一下儲存並運行以啟用捕獲:
FXOS CLI
按照FXOS CLI上的以下步驟配置背板介面上的資料包捕獲:
The following steps on FXOS CLI were used to configure the data packs on the backboard interface:
- 辨識應用程式型別和辨識碼:
firepower# scope ssa
firepower /ssa# show app-instance
App Name Identifier Slot ID Admin State Oper State Running Version Startup Version Deploy Type Turbo Mode Profile Name Cluster State Cluster Role
---------- ---------- ---------- ----------- ---------------- --------------- --------------- ----------- ---------- ------------ --------------- ------------
ftd ftd1 1 Enabled Online 7.2.0.82 7.2.0.82 Native No Not Applicable None
- 建立擷取階段作業:
firepower# scope packet-capture
firepower /packet-capture # create session cap1
firepower /packet-capture/session* # create phy-port Eth1/9
firepower /packet-capture/session/phy-port* # set app ftd
firepower /packet-capture/session/phy-port* # set app-identifier ftd1
firepower /packet-capture/session/phy-port* # up
firepower /packet-capture/session* # create phy-port Eth1/10
firepower /packet-capture/session/phy-port* # set app ftd
firepower /packet-capture/session/phy-port* # set app-identifier ftd1
firepower /packet-capture/session/phy-port* # up
firepower /packet-capture/session* # enable
firepower /packet-capture/session* # commit
firepower /packet-capture/session #
驗證
Verify/strong>
FCM
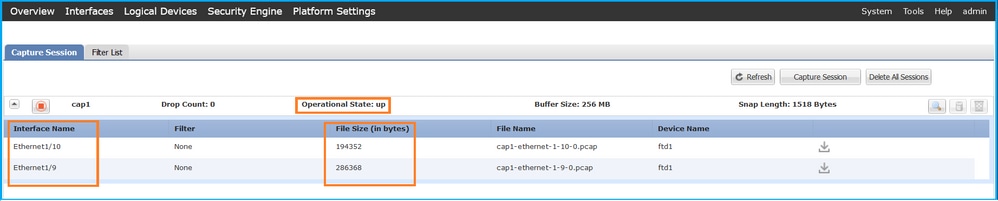
驗證介面名稱,確保Operational Status為up且File Size (in bytes)增加:
Validation of the interface
FXOS CLI
驗證scope packet-capture中的捕獲詳細資訊:
More detailed information on the capture in copet-capture:
firepower# scope packet-capture
firepower /packet-capture # show session cap1
Traffic Monitoring Session:
Packet Capture Session Name: cap1
Session: 1
Admin State: Enabled
Oper State: Up
Oper State Reason: Active
Config Success: Yes
Config Fail Reason:
Append Flag: Overwrite
Session Mem Usage: 256 MB
Session Pcap Snap Len: 1518 Bytes
Error Code: 0
Drop Count: 0
Physical ports involved in Packet Capture:
Slot Id: 1
Port Id: 10
Pcapfile: /workspace/packet-capture/session-1/cap1-ethernet-1-10-0.pcap
Pcapsize: 1017424 bytes
Filter:
Sub Interface: 0
Application Instance Identifier: ftd1
Application Name: ftd
Slot Id: 1
Port Id: 9
Pcapfile: /workspace/packet-capture/session-1/cap1-ethernet-1-9-0.pcap
Pcapsize: 1557432 bytes
Filter:
Sub Interface: 0
Application Instance Identifier: ftd1
Application Name: ftd
收集捕獲檔案
collects capture files
按照收集Firepower 4100/9300內部交換機捕獲檔案部分中的步驟操作。
Collecter of Firepower 4100/9300 internal switchboards in accordance with
捕獲檔案分析
capture file analysis
使用資料包捕獲檔案讀取器應用程式打開捕獲檔案。如果有一個以上的背板介面,請確定開啟每個背板介面的所有擷取檔案。在這種情況下,封包會在背板介面Ethernet1/9上擷取。
Opens the capture file using a file reader application using the data pack. If there is more than one backboard interface, make sure that you open all extraction files for each backboard interface. In this case, the package is retrieved on the backboard interface 1/9.
選擇第一個和第二個資料包,並檢查要點:
Select the first and second data packs and check the key points:
- 捕獲每個ICMP回應請求資料包並顯示2次。
- 原始資料包報頭沒有VLAN標籤。
- 內部交換機插入用於辨識輸出介面Ethernet1/3的附加埠VLAN標籤103。
- 內部開關插入一個附加VN標籤。
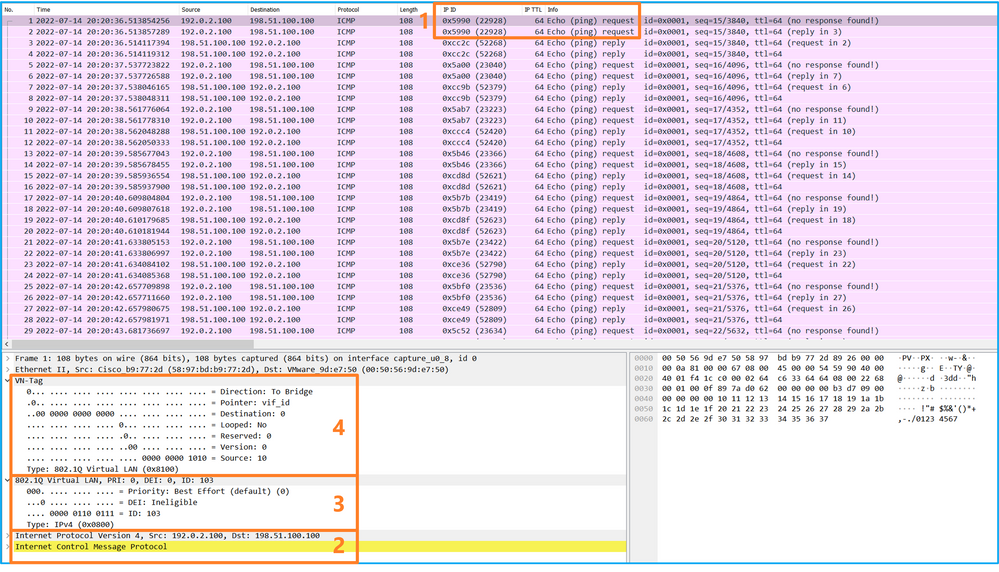
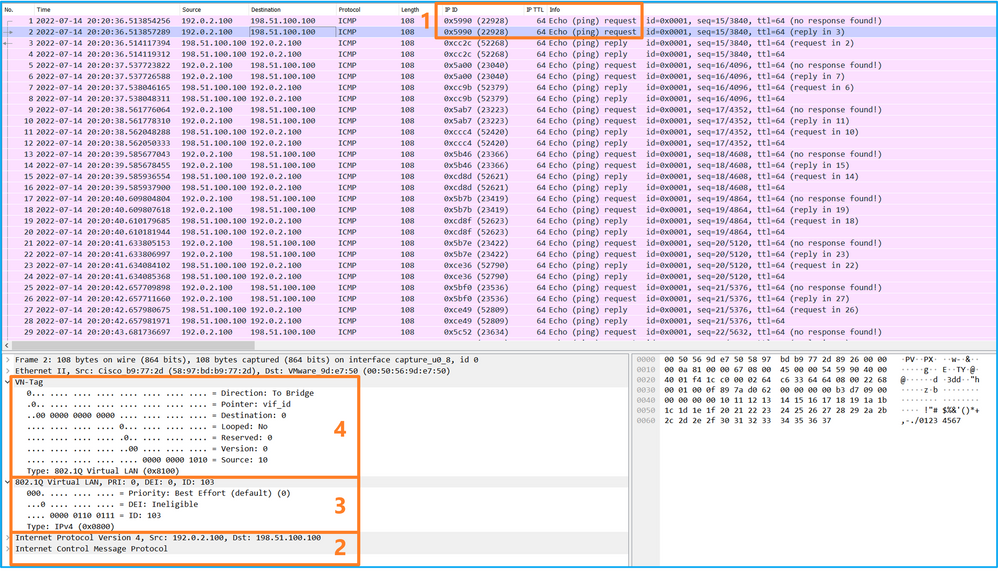
選擇第三和第四個資料包,並檢查要點:
Select the third and fourth packets and check the points:
- 捕獲每個ICMP回應應答並顯示2次。
- 原始資料包報頭沒有VLAN標籤。
- 內部交換機插入用於辨識輸出介面Ethernet1/2的其他埠VLAN標籤102。
- 內部開關插入一個附加VN標籤。
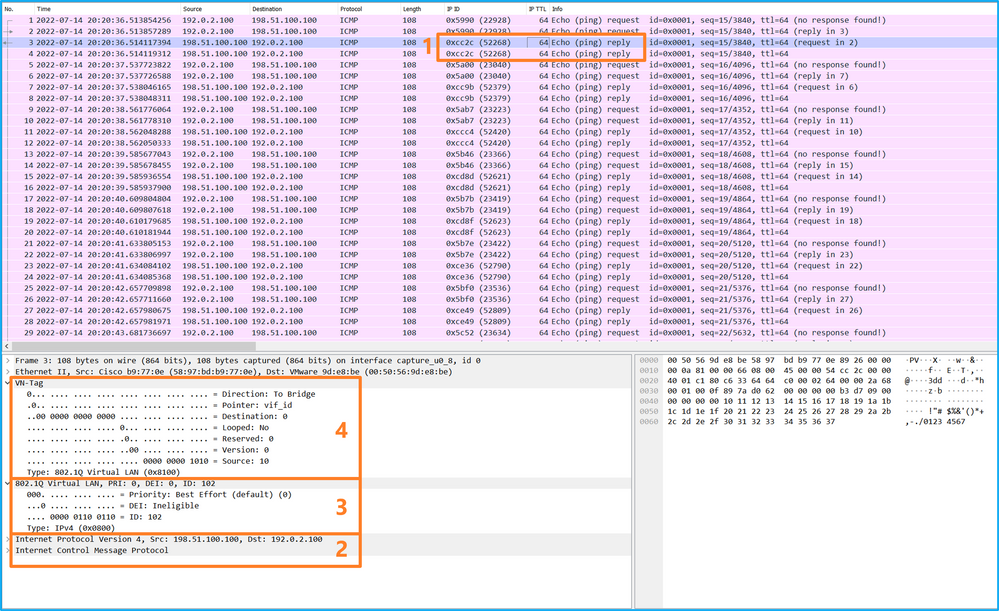
說明
Help
在背板介面上設定封包擷取時,交換器會同時擷取每個封包兩次。在這種情況下,內部交換機將接收安全模組上的應用已標籤了埠VLAN標籤和VN標籤的資料包。VLAN標籤標識內部機箱用於將資料包轉發到網路的輸出介面。ICMP回應請求資料包中的VLAN標籤103將Ethernet1/3標識為輸出介面,而ICMP回應應答資料包中的VLAN標籤102將Ethernet1/2標識為輸出介面。在將資料包轉發到網路之前,內部交換機刪除VN標籤和內部介面VLAN標籤。
In this case, the internal switcher will accept applications from the security module that have been marked as VLAN tags and VN tags. The VLAN tags are used in the internal machine to transfer the package to the network for output. The VLAN tag 103 in the ICMP response request for data requests uses Ethernet1/3 as an input, while the VLAN tag 102 in the ICMP response package uses Ethernet1/2 as an input. Before transferring the package to the Internet, the internal switchboard deletes the VN tag and VLAN tags in the internal interface.
此表格總結列出作業:
The summary of this table lists the homework:
| 工作 |
捕獲點 |
捕獲的資料包中的內部埠VLAN The inside port of the |
方向 |
捕獲的流量 captured traffic |
| 配置並驗證背板介面上的資料包捕獲 Configure and verify bag capture on backboard interface |
背板介面 Backboard Interface |
102 103 |
僅限入口 Access only |
從主機192.0.2.100到主機198.51.100.100的ICMP回應請求 From host 192.02.100 to host 198.51.10.100 ICMP response 從主機198.51.100.100到主機192.0.2.100的ICMP回應應答 ICMP response from host 198.51.10.100 to host 192.02.100 |
如果使用者指定應用捕獲方向,則應用或應用埠資料包捕獲始終配置在背板介面上,並配置在前端介面上。
If the user specifies the direction of the catch, the application or application package is permanently configured on the backboard interface and on the front interface.
主要有2個使用案例:
There are two main cases of use:
- 在背板介面上為離開特定前介面的資料包配置資料包捕獲。例如,在背板介面Ethernet1/9上為離開介面Ethernet1/2的封包設定封包擷取。
- 在特定前介面和背板介面上配置同時資料包捕獲。例如,在介面Ethernet1/2和背板介面Ethernet1/9上為離開介面Ethernet1/2的封包設定同時擷取封包。
本節介紹這兩種使用案例。
This section presents these two cases of use.
任務1
Task 1 / strong / strong / strong / / strong / / strong / / strong / / strong / / strong / / strong / / strong / / strong / / strong / / strong / / strong / / strong
使用FCM和CLI在背板介面上設定和驗證封包擷取。應用程式連線埠Ethernet1/2被辨識為輸出介面的封包會被擷取。在本例中,捕獲ICMP回覆。
Set and verify the package on the backboard interface using FCM and CLI. The application port Ethernet1/2 is identified as the package for the output interface will be seized. In this case, the ICMP reply is captured.
拓撲、資料包流和捕獲點
pings, data packs, catch points
組態
FCM
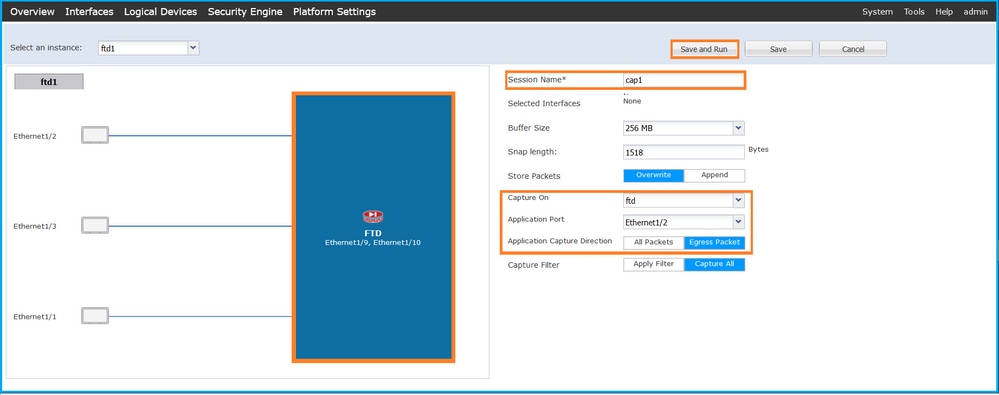
按照FCM上的以下步驟,在FTD應用程式和應用程式連線埠Ethernet1/2上設定封包擷取:
Set package extraction on the FTD application and application port Ethernet1/2 in accordance with the following steps on FCM:
- 使用Tools > Packet Capture > Capture Session建立新的捕獲會話:
- 在Application Port下拉選單中選擇應用程式Ethernet1/2,並在Application Capture Direction中選擇Egress Packet。提供會話名稱,然後按一下儲存並運行以啟用捕獲:
FXOS CLI
按照FXOS CLI上的以下步驟配置背板介面上的資料包捕獲:
The following steps on FXOS CLI were used to configure the data packs on the backboard interface:
- 辨識應用程式型別和辨識碼:
firepower# scope ssa
firepower /ssa# show app-instance
App Name Identifier Slot ID Admin State Oper State Running Version Startup Version Deploy Type Turbo Mode Profile Name Cluster State Cluster Role
---------- ---------- ---------- ----------- ---------------- --------------- --------------- ----------- ---------- ------------ --------------- ------------
ftd ftd1 1 Enabled Online 7.2.0.82 7.2.0.82 Native No Not Applicable None
- 建立擷取階段作業:
firepower# scope packet-capture
firepower /packet-capture # create session cap1
firepower /packet-capture/session* # create app-port 1 l12 Ethernet1/2 ftd
firepower /packet-capture/session/app-port* # set app-identifier ftd1
firepower /packet-capture/session/app-port* # set filter ""
firepower /packet-capture/session/app-port* # set subinterface 0
firepower /packet-capture/session/app-port* # up
firepower /packet-capture/session* # commit
firepower /packet-capture/session #
驗證
Verify/strong>
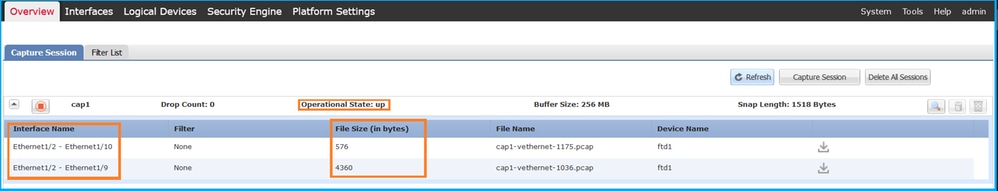
FCM
驗證介面名稱,確保Operational Status為up且File Size (in bytes)增加:
Validation of the interface
FXOS CLI
驗證scope packet-capture中的捕獲詳細資訊:
More detailed information on the capture in copet-capture:
firepower# scope packet-capture
firepower /packet-capture # show session cap1
Traffic Monitoring Session:
Packet Capture Session Name: cap1
Session: 1
Admin State: Enabled
Oper State: Up
Oper State Reason: Active
Config Success: Yes
Config Fail Reason:
Append Flag: Overwrite
Session Mem Usage: 256 MB
Session Pcap Snap Len: 1518 Bytes
Error Code: 0
Drop Count: 0
Application ports involved in Packet Capture:
Slot Id: 1
Link Name: l12
Port Name: Ethernet1/2
App Name: ftd
Sub Interface: 0
Application Instance Identifier: ftd1
Application ports resolved to:
Name: vnic1
Eq Slot Id: 1
Eq Port Id: 9
Pcapfile: /workspace/packet-capture/session-1/cap1-vethernet-1036.pcap
Pcapsize: 53640 bytes
Vlan: 102
Filter:
Name: vnic2
Eq Slot Id: 1
Eq Port Id: 10
Pcapfile: /workspace/packet-capture/session-1/cap1-vethernet-1175.pcap
Pcapsize: 1824 bytes
Vlan: 102
Filter:
收集捕獲檔案
collects capture files
按照收集Firepower 4100/9300內部交換機捕獲檔案部分中的步驟操作。
Collecter of Firepower 4100/9300 internal switchboards in accordance with
捕獲檔案分析
capture file analysis
使用資料包捕獲檔案讀取器應用程式打開捕獲檔案。如果有多個背板介面,請確保打開每個背板介面的所有捕獲檔案。在這種情況下,封包會在背板介面Ethernet1/9上擷取。
Open the capture file using the file reader application for the data pack. If there are multiple backboard interfaces, make sure that you open all capture files for each backboard interface. In this case, the package is retrieved on the backboard interface 1/9 on the Ethernet 1/9.
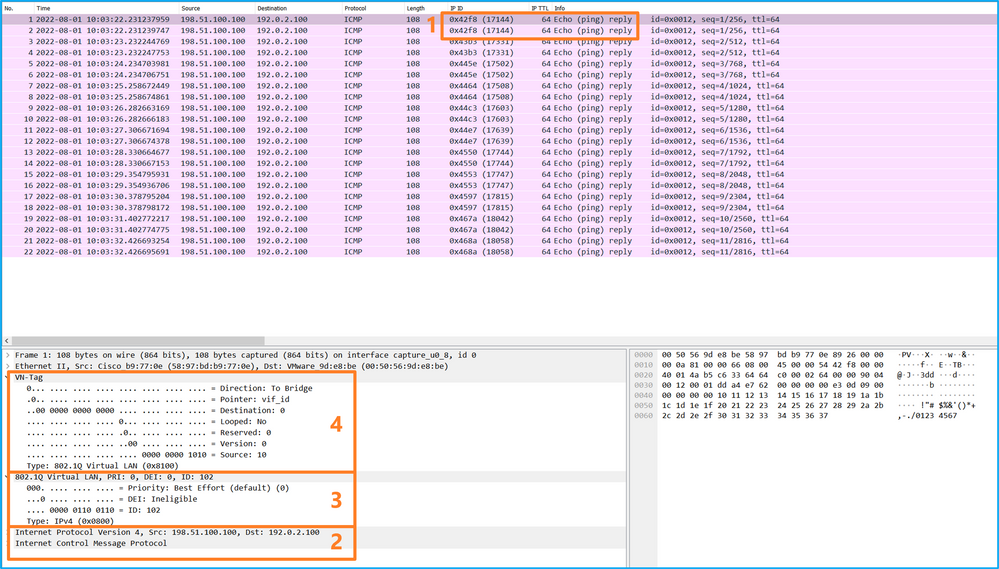
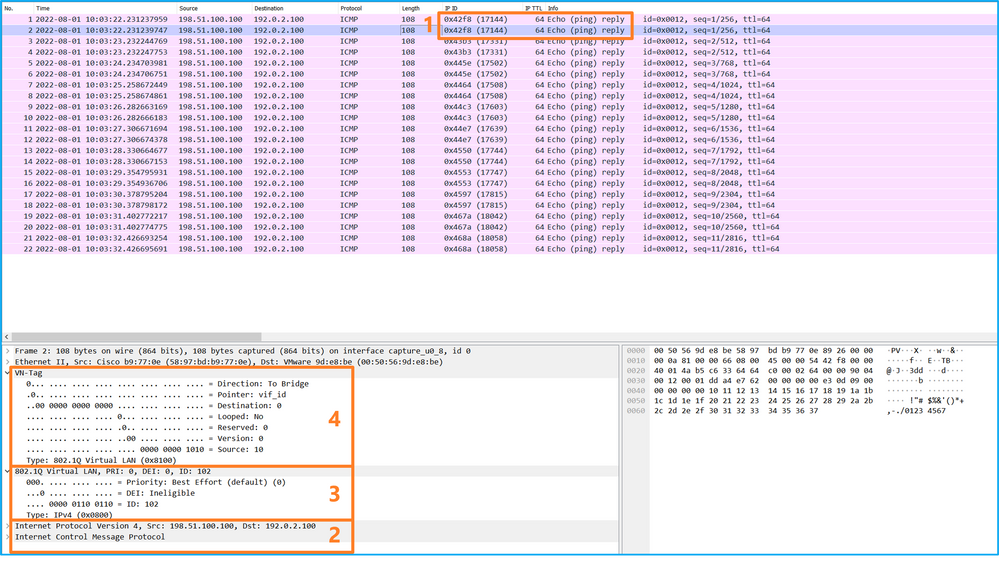
選擇第一個和第二個資料包,並檢查要點:
Select the first and second data packs and check the key points:
- 捕獲每個ICMP回應應答並顯示2次。
- 原始資料包報頭沒有VLAN標籤。
- 內部交換機插入用於辨識輸出介面Ethernet1/2的其他埠VLAN標籤102。
- 內部開關插入一個附加VN標籤。
說明
Help
在這種情況下,連線埠VLAN標籤為102的Ethernet1/2是ICMP回應回覆封包的輸出介面。
In this situation, Ethernet 1/2 of the port VLAN labeled 102 is the ICMP output interface for responding to the package.
當在捕獲選項中將應用程式捕獲方向設定為Egress時,將在入口方向的背板介面上捕獲乙太網報頭中埠VLAN標籤為102的資料包。
When setting application capture directions at Egress in the capture option, the backboard interface in the direction of the entry will capture the data package marked VLAN at 102 in the Aether News portal.
此表格總結列出作業:
The summary of this table lists the homework:
| 工作 |
捕獲點 |
捕獲的資料包中的內部埠VLAN The inside port of the |
方向 |
捕獲的流量 captured traffic |
| 配置並驗證應用和應用程式埠Ethernet1/2上的捕獲資訊 Configure and verify capture information on the application and application port Ethernet1/2 |
背板介面 Backboard Interface |
102 |
僅限入口 Access only |
從主機198.51.100.100到主機192.0.2.100的ICMP回應應答 ICMP response from host 198.51.10.100 to host 192.02.100 |
任務2
Mission 2/strong
使用FCM和CLI在背板介面和正面介面Ethernet1/2上設定和驗證封包擷取。
Set and verify the envelope on the backboard interface and the front interface Ethernet1/2 using FCM and CLI.
同時資料包捕獲配置在:
At the same time, the data pack capture is configured:
- 前介面-捕獲介面Ethernet1/2上埠VLAN 102的資料包。捕獲的資料包是ICMP回應請求。
- 背板介面-會擷取Ethernet1/2辨識為輸出介面的封包,或具有連線埠VLAN 102的封包。捕獲的資料包是ICMP回應應答。
拓撲、資料包流和捕獲點
pings, data packs, catch points

組態
FCM
按照FCM上的以下步驟,在FTD應用程式和應用程式連線埠Ethernet1/2上設定封包擷取:
Set package extraction on the FTD application and application port Ethernet1/2 in accordance with the following steps on FCM:
- 使用Tools > Packet Capture > Capture Session建立新的捕獲會話:
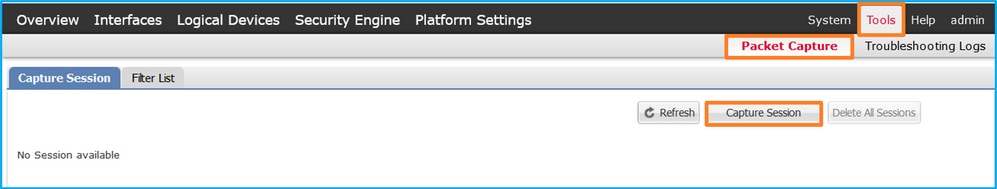
- 在Application Port下拉選單中選擇FTD應用程式Ethernet1/2,然後在Application Capture Direction中選擇All Packets。提供會話名稱,然後按一下儲存並運行以啟用捕獲:
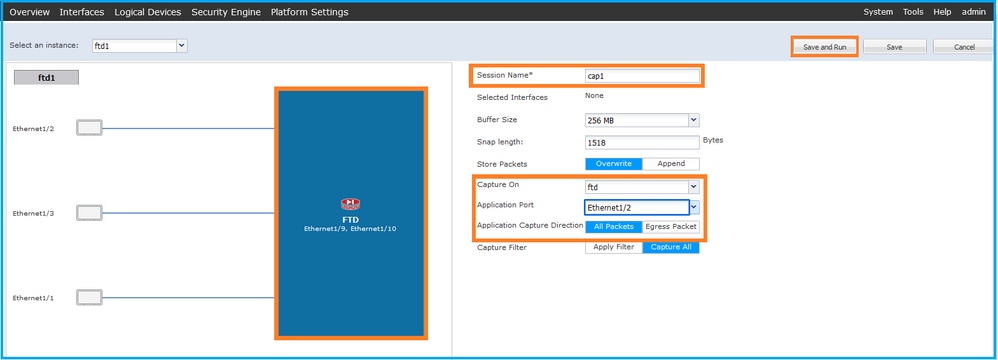
FXOS CLI
按照FXOS CLI上的以下步驟配置背板介面上的資料包捕獲:
The following steps on FXOS CLI were used to configure the data packs on the backboard interface:
- 辨識應用程式型別和辨識碼:
firepower# scope ssa
firepower /ssa# show app-instance
App Name Identifier Slot ID Admin State Oper State Running Version Startup Version Deploy Type Turbo Mode Profile Name Cluster State Cluster Role
---------- ---------- ---------- ----------- ---------------- --------------- --------------- ----------- ---------- ------------ --------------- ------------
ftd ftd1 1 Enabled Online 7.2.0.82 7.2.0.82 Native No Not Applicable None
- 建立擷取階段作業:
firepower# scope packet-capture
firepower /packet-capture # create session cap1
firepower /packet-capture/session* # create phy-port eth1/2
firepower /packet-capture/session/phy-port* # set app-identifier ftd1
firepower /packet-capture/session/phy-port* # exit
firepower /packet-capture/session* # create app-port 1 link12 Ethernet1/2 ftd
firepower /packet-capture/session/app-port* # set app-identifier ftd1
firepower /packet-capture/session* # enable
firepower /packet-capture/session* # commit
firepower /packet-capture/session # commit
驗證
Verify/strong>
FCM
驗證介面名稱,確保Operational Status為up且File Size (in bytes)增加:
Validation of the interface
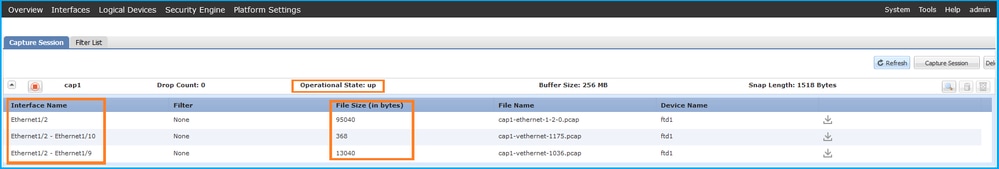
FXOS CLI
驗證scope packet-capture中的捕獲詳細資訊:
More detailed information on the capture in copet-capture:
firepower# scope packet-capture
firepower /packet-capture # show session cap1
Traffic Monitoring Session:
Packet Capture Session Name: cap1
Session: 1
Admin State: Enabled
Oper State: Up
Oper State Reason: Active
Config Success: Yes
Config Fail Reason:
Append Flag: Overwrite
Session Mem Usage: 256 MB
Session Pcap Snap Len: 1518 Bytes
Error Code: 0
Drop Count: 0
Physical ports involved in Packet Capture:
Slot Id: 1
Port Id: 2
Pcapfile: /workspace/packet-capture/session-1/cap1-ethernet-1-2-0.pcap
Pcapsize: 410444 bytes
Filter:
Sub Interface: 0
Application Instance Identifier: ftd1
Application Name: ftd
Application ports involved in Packet Capture:
Slot Id: 1
Link Name: link12
Port Name: Ethernet1/2
App Name: ftd
Sub Interface: 0
Application Instance Identifier: ftd1
Application ports resolved to:
Name: vnic1
Eq Slot Id: 1
Eq Port Id: 9
Pcapfile: /workspace/packet-capture/session-1/cap1-vethernet-1036.pcap
Pcapsize: 128400 bytes
Vlan: 102
Filter:
Name: vnic2
Eq Slot Id: 1
Eq Port Id: 10
Pcapfile: /workspace/packet-capture/session-1/cap1-vethernet-1175.pcap
Pcapsize: 2656 bytes
Vlan: 102
Filter:
收集捕獲檔案
collects capture files
按照收集Firepower 4100/9300內部交換機捕獲檔案部分中的步驟操作。
Collecter of Firepower 4100/9300 internal switchboards in accordance with
捕獲檔案分析
capture file analysis
使用資料包捕獲檔案讀取器應用程式打開捕獲檔案。如果有多個背板介面,請確保打開每個背板介面的所有捕獲檔案。 在這種情況下,封包會在背板介面Ethernet1/9上擷取。
Open the capture file using the file reader application in the data pack. If there are multiple backboard interfaces, make sure that all capture files in each backboard interface are opened. & nbsp; in this case, the envelope will be retrieved on the backboard interface 1/9.
打開介面Ethernet1/2的捕獲檔案,選擇第一個資料包,然後檢查要點:
Open access to Ethernet1/2 capture files, select the first data package and check the point:
- 僅捕獲ICMP回應請求資料包。捕獲每個資料包並顯示2次。
- 原始資料包報頭沒有VLAN標籤。
- 內部交換機插入用於辨識輸入介面Ethernet1/2的其他埠VLAN標籤102。
- 內部開關插入一個附加VN標籤。
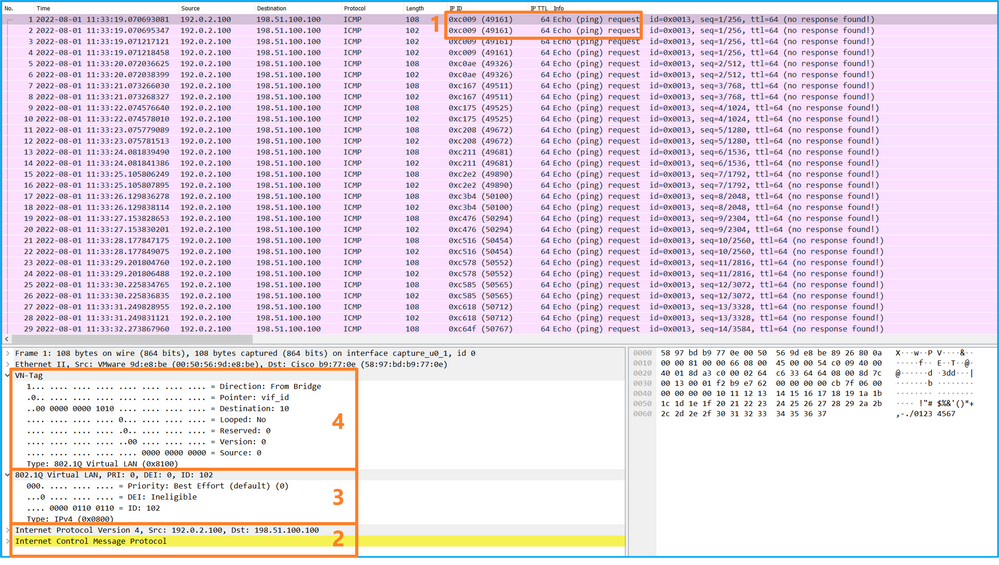
選擇第二個資料包並檢查要點:
Select the second package and check the point:
- 僅捕獲ICMP回應請求資料包。捕獲每個資料包並顯示2次。
- 原始資料包報頭沒有VLAN標籤。
- 內部交換機插入用於辨識輸入介面Ethernet1/2的其他埠VLAN標籤102。

打開介面Ethernet1/9的捕獲檔案,選擇第一個和第二個資料包,然後檢查要點:
Open access to Ethernet1/9 capture files, select the first and second data packs and check the point:
- 捕獲每個ICMP回應應答並顯示2次。
- 原始資料包報頭沒有VLAN標籤。
- 內部交換機插入用於辨識輸出介面Ethernet1/2的其他埠VLAN標籤102。
- 內部開關插入一個附加VN標籤。
說明
Help
如果選擇應用捕獲方向中的所有資料包選項,則會配置與所選應用埠Ethernet1/2相關的2個同時資料包捕獲:前介面Ethernet1/2上的捕獲以及所選背板介面上的捕獲。
If 在前端介面上設定封包擷取時,交換器會同時擷取每個封包兩次: When you set a package on the front interface, the switch will take each package twice at the same time: 按照操作順序,VN標籤在比埠VLAN標籤插入更晚的階段插入。但在捕獲檔案中,帶有VN標籤的資料包比帶有埠VLAN標籤的資料包顯示得更早。在本範例中,ICMP回應要求封包中的VLAN標籤102將Ethernet1/2辨識為輸入介面。 In accordance with the operating order, the VN tag is inserted in a later stage than the port VLAN tag. However, in the captured file, the package with the VN tag is displayed earlier than the package with the port VLAN tag. In this example, ICMP responded to the request that the VLAN tag 102 in the package identify Ethernet1/2 as an interface. 在背板介面上設定封包擷取時,交換器會同時擷取每個封包兩次。內部交換機接收已由安全模組上的應用標籤了埠VLAN標籤和VN標籤的資料包。埠VLAN標籤標識內部機箱用於將資料包轉發到網路的輸出介面。在本例中,ICMP應答資料包中的VLAN標籤102將Ethernet1/2標識為輸出介面。 When you set a package on the backboard interface, the switcher takes each package twice at the same time. The internal switcher receives the package with the port VLAN and VN tags that have been marked by the application on the security module. The port VLAN tags the internal box for sending the package to the output interface. In this case, the VLAN tag 102 in the ICMP responded to the package uses Ethernet 1/2 as an input. 在將資料包轉發到網路之前,內部交換機刪除VN標籤和內部介面VLAN標籤。 Before sending the package to the Internet, the internal switchboard deletes the VN tag and the internal interface VLAN tag. 此表格總結列出作業: The summary of this table lists the homework: 工作 捕獲點 捕獲的資料包中的內部埠VLAN The inside port of the 方向 捕獲的流量 captured traffic 配置並驗證應用和應用程式埠Ethernet1/2上的捕獲資訊 Configure and verify capture information on the application and application port Ethernet1/2 背板介面 Backboard Interface 102 僅限入口 Access only 從主機198.51.100.100到主機192.0.2.100的ICMP回應應答 ICMP response from host 198.51.10.100 to host 192.02.100 Interface Ethernet1/2 102 僅限入口 Access only 從主機192.0.2.100到主機198.51.100.100的ICMP回應請求 From host 192.02.100 to host 198.51.10.100 ICMP response 使用FCM和CLI在子介面Ethernet1/2.205或埠通道子介面Portchannel1.207上配置和驗證資料包捕獲。只有在容器模式下使用FTD應用程式時,才支援子介面上的子介面和擷取。在這種情況下,會在Ethernet1/2.205和Portchannel1.207上設定封包擷取。 FCM and CLI are used to configure and authenticate the data package on the submedial Ethernet 1/2.205 or Portchannel interface Portchannel 1.207. Only when the FTD application is used in the container mode is supported with the submedial interface and extraction. In this case, envelopes are set up on the Ethernet 1/2.205 and Portchannel 1.207. 拓撲、資料包流和捕獲點 pings, data packs, catch points

組態
FCM
按照FCM上的以下步驟,在FTD應用程式和應用程式連線埠Ethernet1/2上設定封包擷取:
Set package extraction on the FTD application and application port Ethernet1/2 in accordance with the following steps on FCM:
- 使用Tools > Packet Capture > Capture Session建立新的捕獲會話:
- 選擇特定應用程式例項ftd1(子介面Ethernet1/2.205),提供會話名稱,然後按一下Save and Run啟用捕獲:

3. 對於埠通道子介面,由於Cisco bug ID CSCvq33119子介面在FCM中是不可見的。使用FXOS CLI在埠通道子介面上配置捕獲。
| 工作 |
捕獲點 |
捕獲的資料包中的內部埠VLAN The inside port of the |
方向 |
捕獲的流量 captured traffic |
| 在子介面Ethernet1/2.205上配置並檢驗資料包捕獲 Configure and verify data pack capture on submedial Ethernet 1/2.205 |
Ethernet1/2.205 |
102 |
僅限入口 Access only |
從主機192.0.2.100到主機198.51.100.100的ICMP回應請求 From host 192.02.100 to host 198.51.10.100 ICMP response |
| 在帶有成員介面Ethernet1/3和Ethernet1/4的Portchannel1子介面上配置並檢驗資料包捕獲 Configure and verify data pack capture on Portchannel 1 interface with Ethernet1/3 and Ethernet1/4 |
Ethernet1/3 Ethernet1/4 |
1001 |
僅限入口 Access only |
從192.168.207.100到主機192.168.207.102的ICMP回應請求 From 192.168.207.100 to host ICMP 192.168.206.102 to respond to requests |
使用FCM和CLI在帶有過濾器的介面Ethernet1/2上配置並驗證資料包捕獲。
Use FCM and CLI to configure and verify data pack captures on the Ethernet1/2 interface with filters.
拓撲、資料包流和捕獲點
pings, data packs, catch points
組態
FCM
按照FCM上的以下步驟,為從主機192.0.2.100到主機198.51.100.100的ICMP回應請求資料包配置捕獲過濾器,並將其應用於介面Ethernet1/2上的資料包捕獲:
In accordance with the following steps on FCM, ICMP packages from host 192.02.100 to host 198.51.10.100 have been configured to capture filters and have been used for the package on interface Ethernet 1/2:
-
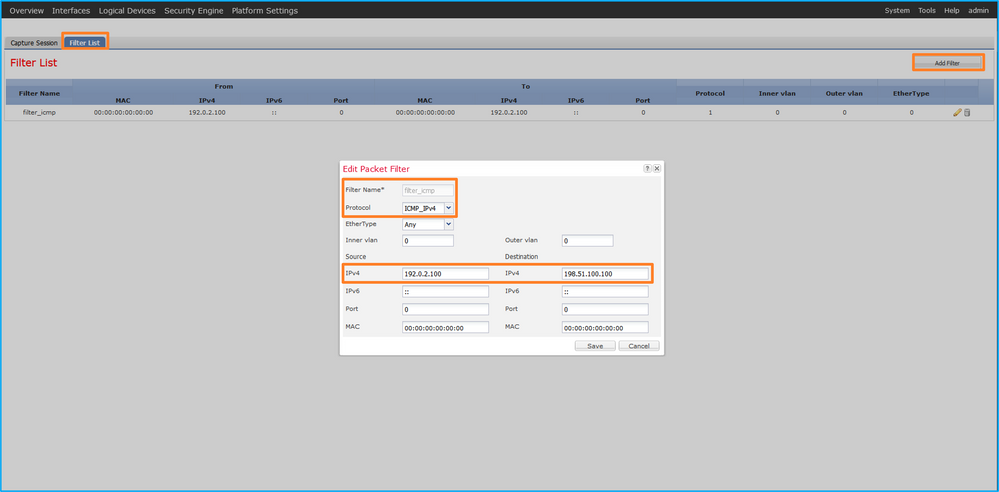
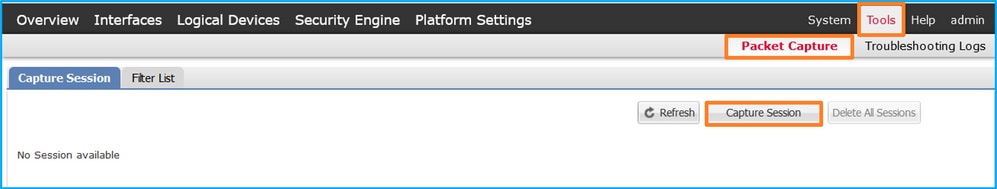
使用Tools > Packet Capture > Filter List > Add Filter建立捕獲過濾器。
Create filters using Tools & gt; Packet Capture & gt; Filter List & gt; Add Filter.
- 指定Filter Name, Protocol, Source IPv4, Destination IPv4,然後按一下Save:
- 使用Tools > Packet Capture > Capture Session建立新的捕獲會話:
- 選擇Ethernet1/2,提供會話名稱,應用捕獲過濾器並按一下Save and Run以啟用捕獲:
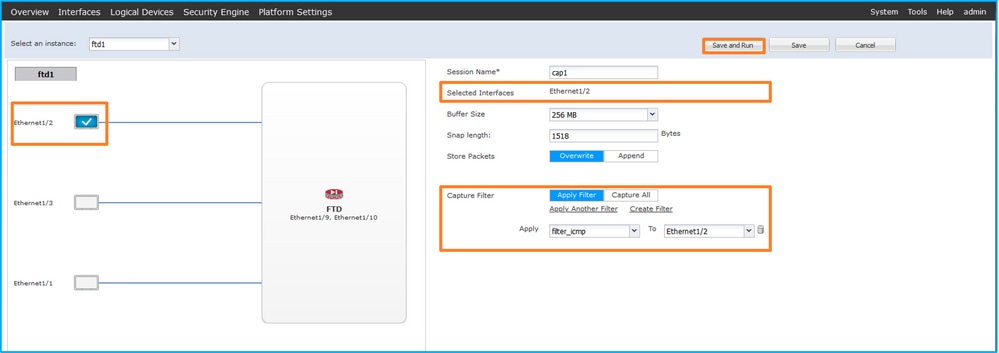
FXOS CLI
按照FXOS CLI上的以下步驟配置背板介面上的資料包捕獲:
The following steps on FXOS CLI were used to configure the data packs on the backboard interface:
- 辨識應用程式型別和辨識碼:
firepower# scope ssa
firepower /ssa# show app-instance
App Name Identifier Slot ID Admin State Oper State Running Version Startup Version Deploy Type Turbo Mode Profile Name Cluster State Cluster Role
---------- ---------- ---------- ----------- ---------------- --------------- --------------- ----------- ---------- ------------ --------------- ------------
ftd ftd1 1 Enabled Online 7.2.0.82 7.2.0.82 Native No Not Applicable None
2. 在https://www.iana.org/assignments/protocol-numbers/protocol-numbers.xhtml中確定IP協定號。在本例中,ICMP協定號是1。
2. The IP protocol number is defined in . In this case, the ICMP protocol number is 1.
3. 建立擷取階段作業:
3. Establishment of the extraction phase:
-
firepower# scope packet-capture
firepower /packet-capture # create filter filter_icmp
firepower /packet-capture/filter* # set destip 198.51.100.100
firepower /packet-capture/filter* # set protocol 1
firepower /packet-capture/filter* # set srcip 192.0.2.100
firepower /packet-capture/filter* # exit
firepower /packet-capture* # create session cap1
firepower /packet-capture/session* # create phy-port Ethernet1/2
firepower /packet-capture/session/phy-port* # set app ftd
firepower /packet-capture/session/phy-port* # set app-identifier ftd1
firepower /packet-capture/session/phy-port* # set filter filter_icmp
firepower /packet-capture/session/phy-port* # exit
firepower /packet-capture/session* # enable
firepower /packet-capture/session* # commit
firepower /packet-capture/session #
驗證
Verify/strong>
FCM
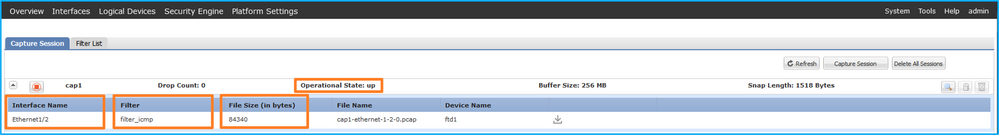
驗證介面名稱,確保Operational Status為up且File Size (in bytes)增加:
Validation of the interface
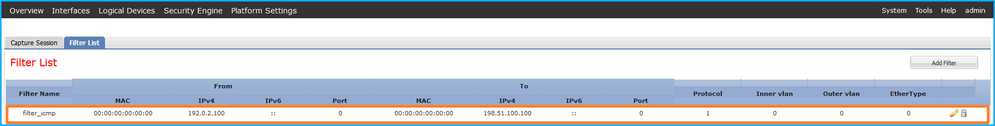
在Tools > Packet Capture > Capture Session中,驗證介面名稱和過濾器,確保Operational Status為up且File Size (bytes)增加:
In
FXOS CLI
驗證scope packet-capture中的捕獲詳細資訊:
More detailed information on the capture in copet-capture:
firepower# scope packet-capture
firepower /packet-capture # show filter detail
Configure a filter for packet capture:
Name: filter_icmp
Protocol: 1
Ivlan: 0
Ovlan: 0
Src Ip: 192.0.2.100
Dest Ip: 198.51.100.100
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Src Ipv6: ::
Dest Ipv6: ::
firepower /packet-capture # show session cap1
Traffic Monitoring Session:
Packet Capture Session Name: cap1
Session: 1
Admin State: Enabled
Oper State: Up
Oper State Reason: Active
Config Success: Yes
Config Fail Reason:
Append Flag: Overwrite
Session Mem Usage: 256 MB
Session Pcap Snap Len: 1518 Bytes
Error Code: 0
Drop Count: 0
Physical ports involved in Packet Capture:
Slot Id: 1
Port Id: 2
Pcapfile: /workspace/packet-capture/session-1/cap1-ethernet-1-2-0.pcap
Pcapsize: 213784 bytes
Filter: filter_icmp
Sub Interface: 0
Application Instance Identifier: ftd1
Application Name: ftd
收集捕獲檔案
collects capture files
按照收集Firepower 4100/9300內部交換機捕獲檔案部分中的步驟操作。
Collecter of Firepower 4100/9300 internal switchboards in accordance with
捕獲檔案分析
capture file analysis
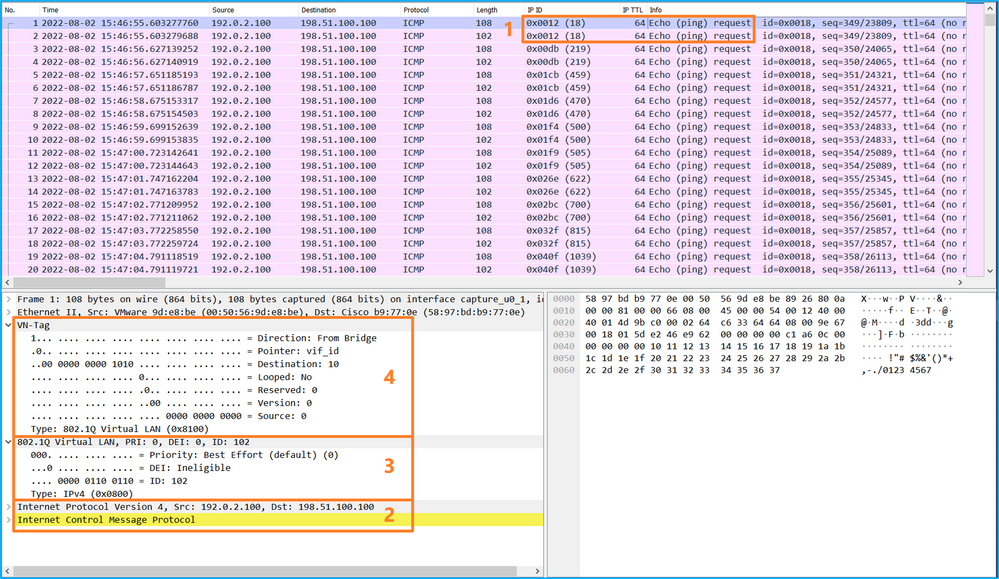
使用資料包捕獲檔案讀取器應用程式打開捕獲檔案。選擇第一個資料包並檢查要點
Open the capture file using the file reader application. Select the first package and check the point
- 僅捕獲ICMP回應請求資料包。捕獲每個資料包並顯示2次。
- 原始資料包報頭沒有VLAN標籤。
- 內部交換機插入用於辨識輸入介面Ethernet1/2的其他埠VLAN標籤102。
- 內部開關插入一個附加VN標籤。
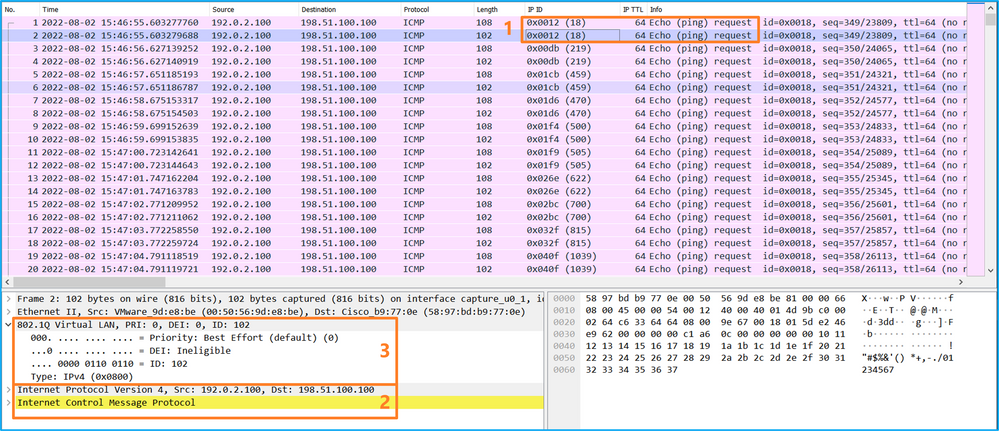
選擇第二個資料包,並檢查要點:
Select the second package and check the point:
- 僅捕獲ICMP回應請求資料包。捕獲每個資料包並顯示2次。
- 原始資料包報頭沒有VLAN標籤。
- 內部交換機插入用於辨識輸入介面Ethernet1/2的其他埠VLAN標籤102。
說明
Help
在前端介面上設定封包擷取時,交換器會同時擷取每個封包兩次:
When you set a package on the front interface, the switch will take each package twice at the same time:
- 在插入埠VLAN標籤之後。
- 在插入VN標籤之後。
按照操作順序,VN標籤在比埠VLAN標籤插入更晚的階段插入。但在捕獲檔案中,帶有VN標籤的資料包比帶有埠VLAN標籤的資料包顯示得更早。
In the operating order, the VN tag is inserted at a later stage than the port VLAN tag. However, in the capture file, the bag with the VN tag is displayed earlier than the bag with the port VLAN tag.
應用捕獲過濾器時,僅捕獲與入口方向上的過濾器匹配的資料包。
When the filter is captured, only the package matching the filter in the direction of the entrance is captured.
此表格總結列出作業:
The summary of this table lists the homework:
| 工作 |
捕獲點 |
捕獲的資料包中的內部埠VLAN The inside port of the |
方向 |
使用者篩選 User Selection |
捕獲的流量 captured traffic |
| 在前介面Ethernet1/2上使用過濾器配置並檢驗資料包捕獲 Used filter configuration and verified data pack capture on front Ethernet1/2 |
Ethernet1/2 |
102 |
僅限入口 Access only |
協定:ICMP Agreed: ICMP 來源:192.0.2.100 Source: 192.2.2.100 目的地: 198.51.100.100 Destination: 198.51.10.100 |
從主機192.0.2.100到主機198.51.100.100的ICMP回應請求 From host 192.02.100 to host 198.51.10.100 ICMP response |
FCM
按照FCM上的以下步驟收集內部交換機捕獲檔案:
Collect internal switchboard capture files according to the following steps on FCM:
- 按一下Disable Session按鈕停止活動捕獲:
- 確保運行狀態為DOWN - Session_Admin_Shut:
- 按一下Download以下載捕獲檔案:
對於埠通道介面,請對每個成員介面重複此步驟。
For port interfaces, repeat this step for each member.
FXOS CLI
按照FXOS CLI上的以下步驟收集捕獲檔案:
Collect capture files according to the following steps on FXOS CLI:
- 停止活動捕獲:
firepower# scope packet-capture
firepower /packet-capture # scope session cap1
firepower /packet-capture/session # disable
firepower /packet-capture/session* # commit
firepower /packet-capture/session # up
firepower /packet-capture # show session cap1 detail
Traffic Monitoring Session:
Packet Capture Session Name: cap1
Session: 1
Admin State: Disabled
Oper State: Down
Oper State Reason: Admin Disable
Config Success: Yes
Config Fail Reason:
Append Flag: Overwrite
Session Mem Usage: 256 MB
Session Pcap Snap Len: 1518 Bytes
Error Code: 0
Drop Count: 0
Physical ports involved in Packet Capture:
Slot Id: 1
Port Id: 2
Pcapfile: /workspace/packet-capture/session-1/cap1-ethernet-1-2-0.pcap
Pcapsize: 115744 bytes
Filter:
Sub Interface: 0
Application Instance Identifier: ftd1
Application Name: ftd
- 從local-mgmt命令作用域上傳捕獲檔案:
firepower# connect local-mgmt
firepower(local-mgmt)# copy /packet-capture/session-1/cap1-ethernet-1-2-0.pcap ?
ftp: Dest File URI
http: Dest File URI
https: Dest File URI
scp: Dest File URI
sftp: Dest File URI
tftp: Dest File URI
usbdrive: Dest File URI
volatile: Dest File URI
workspace: Dest File URI
firepower(local-mgmt)# copy /packet-capture/session-1/cap1-ethernet-1-2-0.pcap ftp://ftpuser@10.10.10.1/cap1-ethernet-1-2-0.pcap
Password:
對於埠通道介面,請為每個成員介面複製捕獲檔案。
For port interfaces, copy files for each member interface.
有關與Firepower 4100/9300內部交換機捕獲相關的準則和限制,請參閱Cisco Firepower 4100/9300 FXOS機箱管理器配置指南或Cisco Firepower 4100/9300 FXOS CLI配置指南的故障排除一章的資料包捕獲部分。
For guidelines and restrictions relating to the capture of the Firepower 4100/9300 internal switchboard, please refer to Cisco Firepower 4100/9300 FXOS box manager configuration guidelines or Cisco Firepower 4100/9300 FXOS CLI configuration guidelines >
這是基於TAC案例中資料包捕獲使用情況的最佳實踐清單:
This is the best list of applications based on data pack capture in the TAC case:
- 瞭解指南和限制。
- 捕獲所有埠通道成員介面上的資料包並分析所有捕獲檔案。
- 使用擷取篩選條件.
- 考慮配置捕獲過濾器時NAT對資料包IP地址的影響。
- 增加或減少用於指定幀大小的Snap Len,以防其與預設值1518位元組不同。較短的大小導致捕獲的資料包數量增加,反之亦然。
- 視需要調整緩衝區大小。
- 請注意FCM或FXOS CLI上的Drop Count。一旦達到緩衝區大小限制,丟棄計數計數器就會增加。
- 在Wireshark上使用過濾器!vntag以僅顯示不帶VN標籤的資料包。這對於在前端介面資料包捕獲檔案中隱藏VN標籤資料包很有用。
- 在Wireshark上使用frame.number&1過濾器僅顯示奇數幀。這對於隱藏背板介面資料包捕獲檔案中的重複資料包很有用。
- 對於TCP之類的協定,Wireshark預設應用著色規則,以不同顏色顯示具有特定條件的資料包。如果由於捕獲檔案中存在重複的資料包而導致內部交換機捕獲,則資料包可能會以誤報的方式進行著色和標籤。如果分析資料包捕獲檔案並應用任何過濾器,則將顯示的資料包導出到新檔案並打開新檔案。
與Firepower 4100/9300不同,安全防火牆3100/4200上的內部交換機捕獲透過capture <name> switch命令在應用程式命令列介面上配置,其中switch選項指定捕獲在內部交換機上配置。
Unlike Firepower 4100/9300, the internal switchboard on the security firewall 3100/4200 has been captured through capture & lt; name > switch commands configured on the application command interface, where switch options specify that the catch is configured on the internal switchboard.
以下是具有switch選項的capture命令:
The following is the order of capture with the option switch:
> capture cap_sw switch ?
buffer Configure size of capture buffer, default is 256MB
ethernet-type Capture Ethernet packets of a particular type, default is IP
interface Capture packets on a specific interface
ivlan Inner Vlan
match Capture packets based on match criteria
ovlan Outer Vlan
packet-length Configure maximum length to save from each packet, default is
64 bytes
real-time Display captured packets in real-time. Warning: using this
option with a slow console connection may result in an
excessive amount of non-displayed packets due to performance
limitations.
stop Stop packet capture
trace Trace the captured packets
type Capture packets based on a particular type
<cr>
資料包捕獲配置的一般步驟如下:
The general steps taken to capture the package are as follows:
- 指定入口介面:
交換機捕獲配置接受輸入介面nameif。使用者可以指定資料介面名稱、內部上行鏈路或管理介面:
The switcher capture configuration accepts the interface nameif. The user can specify a data interface name, an internal uplink or an administrative interface:
> capture capsw switch interface ?
Available interfaces to listen:
in_data_uplink1 Capture packets on internal data uplink1 interface
in_mgmt_uplink1 Capture packets on internal mgmt uplink1 interface
inside Name of interface Ethernet1/1.205
management Name of interface Management1/1
安全防火牆4200支援雙向捕獲。除非另有指定,否則預設值為ingress:
The security firewall 4200 supports two-way capture. Unless otherwise specified, the default value is ingress:
> capture capi switch interface inside direction
both To capture switch bi-directional traffic
egress To capture switch egressing traffic
ingress To capture switch ingressing traffic
此外,安全防火牆4245具有2個內部資料和2個管理上行鏈路介面:
In addition, security firewall 4245 has 2 internal data and 2
> capture capsw switch interface
eventing Name of interface Management1/2
in_data_uplink1 Capture packets on internal data uplink1 interface
in_data_uplink2 Capture packets on internal data uplink2 interface
in_mgmt_uplink1 Capture packets on internal mgmt uplink1 interface
in_mgmt_uplink2 Capture packets on internal mgmt uplink2 interface
management Name of interface Management1/1
- 指定乙太網幀EtherType。預設EtherType為IP。ethernet-type選項值指定EtherType:
> capture capsw switch interface inside ethernet-type ?
802.1Q
<0-65535> Ethernet type
arp
ip
ip6
pppoed
pppoes
rarp
sgt
vlan
- 指定匹配條件。捕獲匹配選項指定匹配條件:
> capture capsw switch interface inside match ?
<0-255> Enter protocol number (0 - 255)
ah
eigrp
esp
gre
icmp
icmp6
igmp
igrp
ip
ipinip
ipsec
mac Mac-address filter
nos
ospf
pcp
pim
pptp
sctp
snp
spi SPI value
tcp
udp
<cr>
- 指定其他可選引數,例如緩衝區大小、資料包長度等。
- 啟用捕獲。no capture <name> switch stop命令會啟用捕獲:
> capture capsw switch interface inside match ip
> no capture capsw switch stop
- 驗證捕獲詳細資訊:
- 管理狀態為enabled,操作狀態為up和活動。
- 資料包捕獲檔案大小 Pcapsize增加。
- show capture <cap_name>的輸出中捕獲的資料包數非零。
- 擷取路徑Pcapfile。捕獲的資料包將自動儲存在/mnt/disk0/packet-capture/資料夾中。
- 捕獲條件。軟體將根據捕獲條件自動建立捕獲過濾器。
> show capture capsw
27 packet captured on disk using switch capture
Reading of capture file from disk is not supported
> show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: enabled
Oper State: up
Oper State Reason: Active
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 1
Physical port:
Slot Id: 1
Port Id: 1
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap
Pcapsize: 18838
Filter: capsw-1-1
Packet Capture Filter Info
Name: capsw-1-1
Protocol: 0
Ivlan: 0
Ovlan: 205
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
0 packet captured on disk using switch capture
Reading of capture file from disk is not supported
- 必要時停止捕獲:
> capture capsw switch stop
> show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: disabled
Oper State: down
Oper State Reason: Session_Admin_Shut
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 1
Physical port:
Slot Id: 1
Port Id: 1
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap
Pcapsize: 24
Filter: capsw-1-1
Packet Capture Filter Info
Name: capsw-1-1
Protocol: 0
Ivlan: 0
Ovlan: 205
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
0 packet captured on disk using switch capture
Reading of capture file from disk is not supported
8. 收集擷取檔案。按照收集安全防火牆內部交換機捕獲檔案部分中的步驟操作。
在安全防火牆軟體版本7.4中,FMC或FDM不支援內部交換機捕獲配置。在ASA軟體版本9.18(1)及更高版本中,可以在ASDM版本7.18.1.x及更高版本中配置內部交換機捕獲。
In version 7.4 of the security firewall software, FMC or FDM does not support in-house switch capture. In version 9.18 (1) and above of the ASA software, inside switch capture can be configured in version 7.18.1.x and above of the ASDM software.
這些場景包括安全防火牆3100/4200內部交換機捕獲的常見使用案例。
These scenes include common usage cases captured by the security firewall 3100/4200 inside the switchboard.
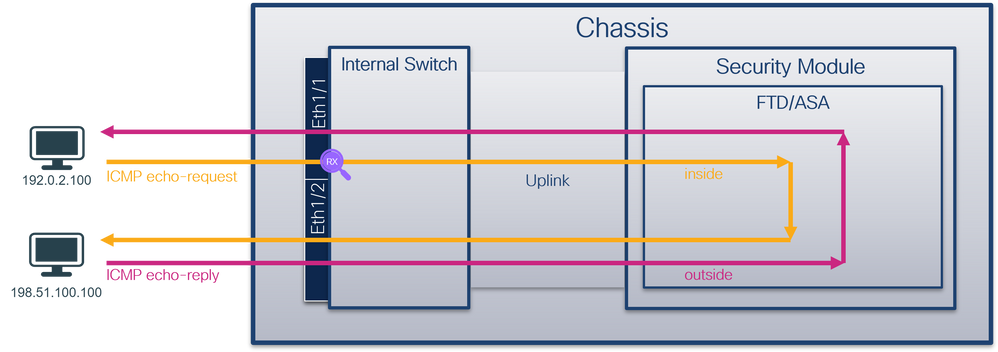
使用FTD或ASA CLI在介面Ethernet1/1或Portchannel1介面上配置和驗證資料包捕獲。兩個介面都具有nameif inside。
Configure and authenticate the data packs using the FTD or ASA CLI interface 1/1 or Portchannel1. Both interfaces have the nameif inside.
拓撲、資料包流和捕獲點
pings, data packs, catch points
安全防火牆3100:
Security firewall 3100:
具有雙向捕獲功能的安全防火牆4200:
Safety firewall 4200 with two-way capture function:
組態
在ASA或FTD CLI上執行以下步驟,在介面Ethernet1/1或Port-channel1上配置資料包捕獲:
Run the following steps on ASA or FTD CLI and configure the data pack on interface Ethernet1/1 or Port-channel1:
- 驗證nameif:
> show nameif
Interface Name Security
Ethernet1/1 inside 0
Ethernet1/2 outside 0
Management1/1 diagnostic 0
> show nameif
Interface Name Security
Port-channel1 inside 0
Ethernet1/2 outside 0
Management1/1 diagnostic 0
- 建立擷取階段作業
> capture capsw switch interface inside
安全防火牆4200支援捕獲方向性:
Security firewall 4200 supports capture directional:
> capture capsw switch interface inside direction ?
both To capture switch bi-directional traffic
egress To capture switch egressing traffic
ingress To capture switch ingressing traffic
> capture capsw switch interface inside direction both
- 啟用擷取階段作業:
> no capture capsw switch stop
驗證
Verify/strong>
驗證捕獲會話名稱、管理和操作狀態、介面插槽和識別符號。確保Pcapsize值(以位元組為單位)增加且捕獲的資料包數非零:
Verify to capture session names, management and operating status, interface slots and identifiers. Ensure that the value of Pcapsize (in bytes) is increased and the number of packages captured is not zero:
> show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: enabled
Oper State: up
Oper State Reason: Active
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 1
Physical port:
Slot Id: 1
Port Id: 1
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap
Pcapsize: 12653
Filter: capsw-1-1
Packet Capture Filter Info
Name: capsw-1-1
Protocol: 0
Ivlan: 0
Ovlan: 0
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
79 packets captured on disk using switch capture
Reading of capture file from disk is not supported
安全防火牆4200:
Security firewall 4200:
> show cap capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: enabled
Oper State: up
Oper State Reason: Active
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 1
Physical port:
Slot Id: 1
Port Id: 1
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap
Pcapsize: 0
Direction: both
Drop: disable
Filter: capsw-1-1
Packet Capture Filter Info
Name: capsw-1-1
Protocol: 0
Ivlan: 0
Ovlan: 0
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
33 packet captured on disk using switch capture
Reading of capture file from disk is not supported
對於Port-channel1,捕獲在所有成員介面上配置:
For Port-channel1, capture is configured on all member interfaces:
> show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: enabled
Oper State: up
Oper State Reason: Active
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 2
Physical port:
Slot Id: 1
Port Id: 4
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-4-0.pcap
Pcapsize: 28824
Filter: capsw-1-4
Packet Capture Filter Info
Name: capsw-1-4
Protocol: 0
Ivlan: 0
Ovlan: 0
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Physical port:
Slot Id: 1
Port Id: 3
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-3-0.pcap
Pcapsize: 18399
Filter: capsw-1-3
Packet Capture Filter Info
Name: capsw-1-3
Protocol: 0
Ivlan: 0
Ovlan: 0
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
56 packet captured on disk using switch capture
Reading of capture file from disk is not supported
可以在FXOS local-mgmt命令外殼中透過show portchannel summary 命令驗證埠通道成員介面:
A port channel interface can be verified through the FXOS local-mgmt command shell via how portchannel submary command channel interface:
> connect fxos
…
firewall# connect local-mgmt
firewall(local-mgmt)# show portchannel summary
Flags: D - Down P - Up in port-channel (members)
I - Individual H - Hot-standby (LACP only)
s - Suspended r - Module-removed
S - Switched R - Routed
U - Up (port-channel)
M - Not in use. Min-links not met
-------------------------------------------------------------------------------
Group Port- Type Protocol Member Ports
Channel
--------------------------------------------------------------------------------
1 Po1(U) Eth LACP Eth1/3(P) Eth1/4(P)
LACP KeepAlive Timer:
--------------------------------------------------------------------------------
Channel PeerKeepAliveTimerFast
--------------------------------------------------------------------------------
1 Po1(U) False
Cluster LACP Status:
--------------------------------------------------------------------------------
Channel ClusterSpanned ClusterDetach ClusterUnitID ClusterSysID
--------------------------------------------------------------------------------
1 Po1(U) False False 0 clust
要訪問ASA上的FXOS,請運行connect fxos admin命令。如果是多情景,請在管理情景中運行命令。
To interview FXOS on ASA, run the command contract fxos admin command. If there are multiple scenarios, run the command in the management scenario.
收集捕獲檔案
collects capture files
按照收集安全防火牆內部交換機捕獲檔案部分中的步驟操作。
Collect security firewall internal switches according to to capture step operations in part of the file . & nbsp;
捕獲檔案分析
capture file analysis
使用資料包捕獲檔案讀取器應用程式打開Ethernet1/1的捕獲檔案。在本示例中,分析安全防火牆3100上捕獲的資料包。選擇第一個資料包並檢查要點:
Use the data pack to capture the file reader application to open the Ethernet1/1 capture file. In this example, analyze the package captured on the safety firewall 3100. Select the first package and check the point:
- 僅捕獲ICMP回應請求資料包。
- 原始資料包報頭沒有VLAN標籤。
打開Portchannel1成員介面的捕獲檔案。選擇第一個資料包並檢查要點:
Opens the capture file of the Portchannel1 interface. Select the first package and check the point:
- 僅捕獲ICMP回應請求資料包。
- 原始資料包報頭沒有VLAN標籤。
說明
Help
交換器擷取是在介面Ethernet1/1或Portchannel1上設定。
Swap capture is set on interface Ethernet1/1 or Portchannel1.
此表格總結列出作業:
The summary of this table lists the homework:
| 工作 |
捕獲點 |
內部篩選器 Internal Selector |
方向 |
捕獲的流量 captured traffic |
| 在介面Ethernet1/1上配置並檢驗資料包捕獲 Configure and verify data pack capture on interface Ethernet1/1 |
Ethernet1/1 |
無 None |
僅限入口* Access only* |
從主機192.0.2.100到主機198.51.100.100的ICMP回應請求 From host 192.02.100 to host 198.51.10.100 ICMP response |
| 在介面Portchannel1上配置並檢驗帶有成員介面Ethernet1/3和Ethernet1/4的資料包捕獲 Configure and test data pack capture on interface Portchannel1 with user interfaces Ethernet1/3 and Ethernet1/4 |
Ethernet1/3 Ethernet1/4 |
無 None |
僅限入口* Access only* |
從主機192.0.2.100到主機198.51.100.100的ICMP回應請求 From host 192.02.100 to host 198.51.10.100 ICMP response |
* 與3100不同,安全防火牆4200支援雙向(入口和出口)捕獲。
* Unlike 3100, the security firewall 4200 backstops two-way (entry and exit) captures.
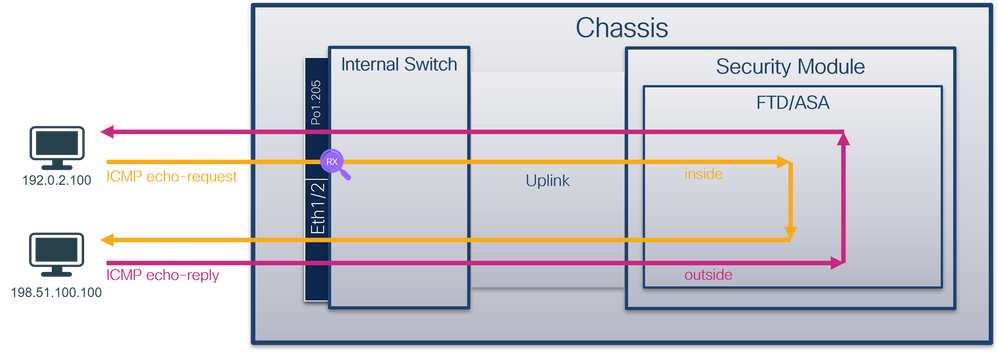
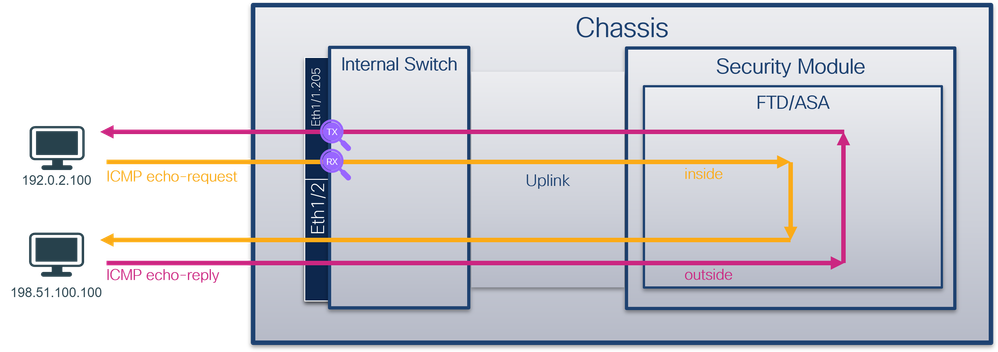
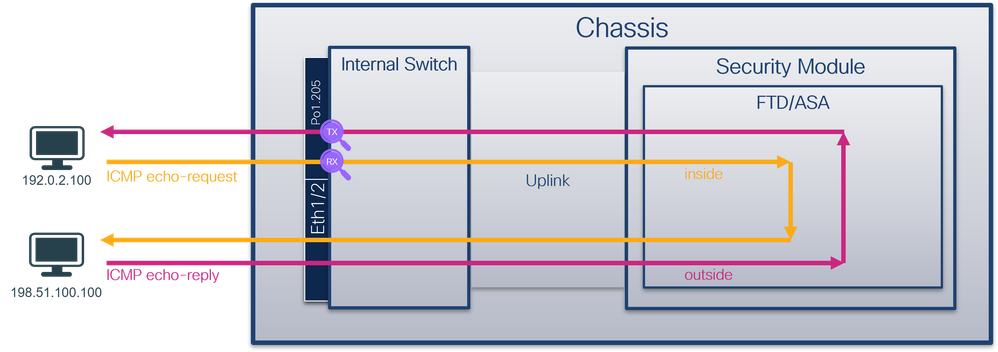
使用FTD或ASA CLI配置和驗證子介面Ethernet1/1.205或Portchannel1.205上的資料包捕獲。兩個子介面都有nameif inside。
You can use the FTD or ASA CLI to configure and authenticate the data packs on the Ethernet 1/1.205 or Portchannel 1.205. Both have the nameif inside.
拓撲、資料包流和捕獲點
pings, data packs, catch points
安全防火牆3100:
Security firewall 3100:

安全防火牆4200:
Security firewall 4200:
組態
在ASA或FTD CLI上執行以下步驟,在介面Ethernet1/1或Port-channel1上配置資料包捕獲:
Run the following steps on ASA or FTD CLI and configure the data pack on interface Ethernet1/1 or Port-channel1:
- 驗證nameif:
> show nameif
Interface Name Security
Ethernet1/1.205 inside 0
Ethernet1/2 outside 0
Management1/1 diagnostic 0
> show nameif
Interface Name Security
Port-channel1.205 inside 0
Ethernet1/2 outside 0
Management1/1 diagnostic 0
- 建立擷取階段作業:
> capture capsw switch interface inside
安全防火牆4200支援捕獲方向性:
Security firewall 4200 supports capture directional:
> capture capsw switch interface inside direction ?
both To capture switch bi-directional traffic
egress To capture switch egressing traffic
ingress To capture switch ingressing traffic
> capture capsw switch interface inside direction both
3. 啟用擷取階段作業:
3. Initiation of extraction phase:
> no capture capsw switch stop
驗證
Verify/strong>
驗證捕獲會話名稱、管理和操作狀態、介面插槽和識別符號。確保Pcapsize值(以位元組為單位)增加且捕獲的資料包數非零:
Verify to capture session names, management and operating status, interface slots and identifiers. Ensure that the value of Pcapsize (in bytes) is increased and the number of packages captured is not zero:
> show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: enabled
Oper State: up
Oper State Reason: Active
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 1
Physical port:
Slot Id: 1
Port Id: 1
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap
Pcapsize: 6360
Filter: capsw-1-1
Packet Capture Filter Info
Name: capsw-1-1
Protocol: 0
Ivlan: 0
Ovlan: 205
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
46 packets captured on disk using switch capture
Reading of capture file from disk is not supported
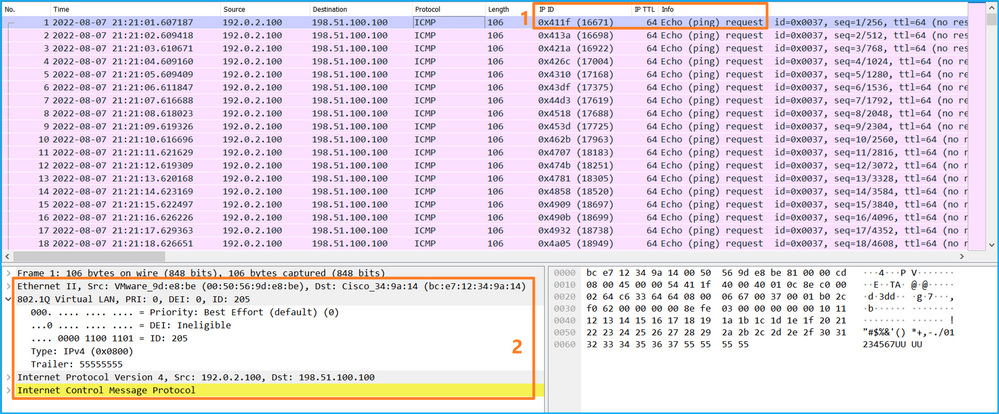
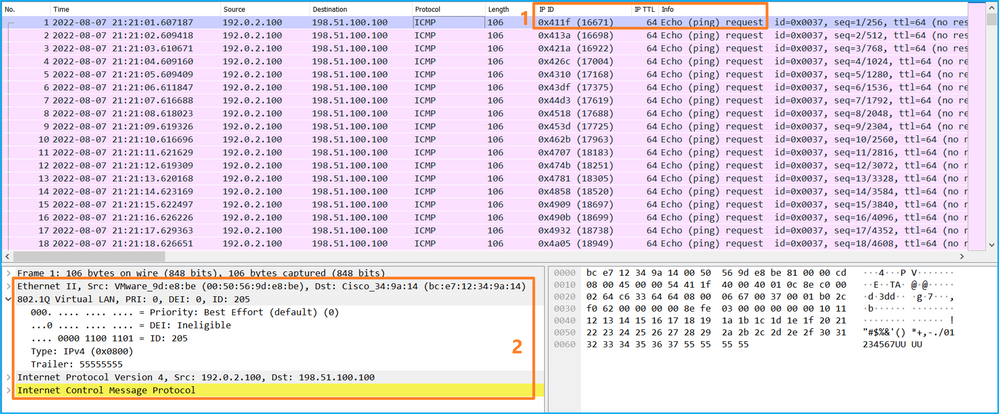
在這種情況下,會建立一個外部VLAN Ovlan=205的過濾器並應用於介面。
In this case, an external VLANOvlan=205
對於Port-channel1,在所有成員介面上配置了帶過濾器Ovlan=205的捕獲: For Port-channel1, captures with filter Ovlan=205 have been placed on all member interfaces: 可以在FXOS local-mgmt命令外殼中透過show portchannel summary 命令驗證埠通道成員介面: A port channel interface can be verified through the FXOS local-mgmt command shell via how portchannel submary command channel interface: 要訪問ASA上的FXOS,請運行connect fxos admin命令。如果是多情景,請在管理情景中運行此命令。 To interview FXOS on ASA, run the command contract fxos admin command. If there are multiple scenarios, run this command in the management scenario. 收集捕獲檔案 collects capture files 按照收集安全防火牆內部交換機捕獲檔案部分中的步驟操作。 Collect security firewall internal switches according to to capture step operations in part of the file . & nbsp; 捕獲檔案分析 capture file analysis 使用資料包捕獲檔案讀取器應用程式打開Ethernet1/1.205的捕獲檔案。在本示例中,分析安全防火牆3100上捕獲的資料包。選擇第一個資料包並檢查要點: Use the data pack to capture the file reader application to open the Ethernet 1/1.205 capture file. In this example, analyze the package captured on the safety firewall 3100. Select the first package and check the point: 打開Portchannel1成員介面的捕獲檔案。選擇第一個資料包並檢查要點: Opens the capture file of the Portchannel1 interface. Select the first package and check the point: 說明 Help 使用與外部VLAN 205匹配的過濾器在子介面Ethernet1/1.205或Portchannel1.205上配置交換機捕獲。 A filter matching the external VLAN 205 is used to configure a switchboard capture on the submedian Ethernet 1/1.205 or Portchannel 1.205. 此表格總結列出作業: The summary of this table lists the homework: 工作 捕獲點 內部篩選器 Internal Selector 方向 捕獲的流量 captured traffic 在子介面Ethernet1/1.205上配置並檢驗資料包捕獲 Configure and verify data pack capture on submedial Ethernet 1/1.205 Ethernet1/1 外部VLAN 205 External VLAN 205 僅限入口* Access only* 從主機192.0.2.100到主機198.51.100.100的ICMP回應請求 From host 192.02.100 to host 198.51.10.100 ICMP response 在子介面Portchannel1.205上配置並檢驗帶有成員介面Ethernet1/3和Ethernet1/4的資料包捕獲 Configure and test data packs with user interfaces Ethernet1/3 and Ethernet1/4 on the submedial Portchannel 1.205 Ethernet1/3 Ethernet1/4 外部VLAN 205 External VLAN 205 僅限入口* Access only* 從主機192.0.2.100到主機198.51.100.100的ICMP回應請求 From host 192.02.100 to host 198.51.10.100 ICMP response * 與3100不同,安全防火牆4200支援雙向(入口和出口)捕獲。 * Unlike 3100, the security firewall 4200 backstops two-way (entry and exit) captures. 安全防火牆3100有2個內部介面: Security firewall 3100 has two internal interfaces: Secure Firewall 4200最多有4個內部介面: Secure Firewall 4200 with up to four internal interfaces: 任務1 Task 1 / strong / strong / strong / / strong / / strong / / strong / / strong / / strong / / strong / / strong / / strong / / strong / / strong / / strong / / strong 使用FTD或ASA CLI在上行鏈路介面in_data_uplink1上配置和驗證資料包捕獲。 Configure and authenticate the data package using the FTD or ASA CLI on the upper-link interface in_data_uplink1. 拓撲、資料包流和捕獲點 pings, data packs, catch points 安全防火牆3100: Security firewall 3100: 安全防火牆4200: Security firewall 4200: 組態 在ASA或FTD CLI上執行以下步驟,在in_data_uplink1介面上配置資料包捕獲: The following steps were carried out on ASA or FTD CLI to configure the package on the in_data_uplink1 interface: 安全防火牆4200支援捕獲方向性: Security firewall 4200 supports capture directional: 2. 啟用捕獲會話: 2. Enable capture sessions: 驗證 Verify/strong> 驗證捕獲會話名稱、管理和操作狀態、介面插槽和識別符號。確保Pcapsize值(以位元組為單位)增加且捕獲的資料包數非零: Verify to capture session names, management and operating status, interface slots and identifiers. Ensure that the value of Pcapsize (in bytes) is increased and the number of packages captured is not zero: 在這種情況下,會在具有內部ID 18的介面上建立捕獲,內部ID是Secure Firewall 3130上的in_data_uplink1介面。FXOS local-mgmt命令外殼中的show portmanager switch status命令顯示介面ID: In this case, a catch will be established on an interface with internal ID 要訪問ASA上的FXOS,請運行connect fxos admin命令。如果是多情景,請在管理情景中運行此命令。 To interview FXOS on ASA, run the command contract fxos admin command. If there are multiple scenarios, run this command in the management scenario. 收集捕獲檔案 collects capture files 按照收集安全防火牆內部交換機捕獲檔案部分中的步驟操作。 Collect security firewall internal switches according to to capture step operations in part of the file . & nbsp; 捕獲檔案分析 capture file analysis 使用資料包捕獲檔案讀取器應用程式打開介面in_data_uplink1的捕獲檔案。在本示例中,分析安全防火牆3100上捕獲的資料包。 Opens the catch file for interface in_data_uplink1 using the file reader application. In this example, analyse the package captured on the safety firewall 3100. 檢查要點-在本例中,捕獲ICMP回應請求和應答資料包。這些是從應用傳送到內部交換機的資料包。 Check points - In this case, get an ICMP response request and answer package. These are the packages that are sent from the application to the internal switchboard. 說明 Help 當在上行鏈路介面上配置交換機捕獲時,僅捕獲從應用傳送到內部交換機的資料包。不會捕獲傳送到應用程式的資料包。 When equipped with a switchboard capture on the upper link interface, only the package sent from the application to the internal switchboard is captured. The package sent to the application is not captured. 此表格總結列出作業: The summary of this table lists the homework: 工作 捕獲點 內部篩選器 Internal Selector 方向 捕獲的流量 captured traffic 在in_data_uplink1上行鏈路介面上配置並檢驗資料包捕獲 Configure and verify data pack capture on the line link interface on in_data_uplink1 in_data_uplink1 無 None 僅限入口* Access only* 從主機192.0.2.100到主機198.51.100.100的ICMP回應請求 From host 192.02.100 to host 198.51.10.100 ICMP response 從主機198.51.100.100到主機192.0.2.100的ICMP回應應答 ICMP response from host 198.51.10.100 to host 192.02.100 * 與3100不同,安全防火牆4200支援雙向(入口和出口)捕獲。 * Unlike 3100, the security firewall 4200 backstops two-way (entry and exit) captures. 任務2 Mission 2/strong 使用FTD或ASA CLI在上行鏈路介面in_mgmt_uplink1上配置和驗證資料包捕獲。僅捕獲管理平面連線的資料包。 uses the FTD or ASA CLI to configure and authenticate the data packets on the upper link interface in_mgmt_uplink1. 拓撲、資料包流和捕獲點 pings, data packs, catch points 安全防火牆3100: Security firewall 3100: 安全防火牆4200: Security firewall 4200: 組態 在ASA或FTD CLI上執行以下步驟,在in_mgmt_uplink1介面上配置資料包捕獲: The following steps were carried out on ASA or FTD CLI to configure the data package on the interface in_mgmt_uplink1: 安全防火牆4200支援捕獲方向性: Security firewall 4200 supports capture directional: 2. 啟用擷取階段作業: 2. Initiation of extraction phase: 驗證 Verify/strong> 驗證捕獲會話名稱、管理和操作狀態、介面插槽和識別符號。確保Pcapsize值(以位元組為單位)增加且捕獲的資料包數非零: Verify to capture session names, management and operating status, interface slots and identifiers. Ensure that the value of Pcapsize (in bytes) is increased and the number of packages captured is not zero: 在這種情況下,會在介面上使用內部ID 19建立捕獲,內部ID 19是安全防火牆3130上的in_mgmt_uplink1介面。FXOS local-mgmt命令外殼中的show portmanager switch status命令顯示介面ID: In this case, an internal ID 19 will be used to create a catch on the interface. The internal ID 19 is the interface ID on the security firewall 3130 at 要訪問ASA上的FXOS,請運行connect fxos admin命令。如果是多情景,請在管理情景中運行此命令。 To interview FXOS on ASA, run the command contract fxos admin command. If there are multiple scenarios, run this command in the management scenario. 收集捕獲檔案 collects capture files 按照收集安全防火牆內部交換機捕獲檔案部分中的步驟操作。 & nbsp; 捕獲檔案分析 capture file analysis 使用資料包捕獲檔案讀取器應用程式打開介面in_mgmt_uplink1的捕獲檔案。在本示例中,分析安全防火牆3100上捕獲的資料包。 Opens the capture file using the data pack to capture file readers application for interface in_mgmt_uplink1. In this example, analyse the data packs captured on the safety firewall 3100. 檢查要點-在這種情況下,僅顯示來自管理IP地址192.0.2.200的資料包。例如SSH、Sftunnel或ICMP回應應答資料包。這些資料包是從應用管理介面透過內部交換機傳送到網路的。 Check points - In this case, only data packages from the IP management address 192.02.200 are shown. For example, SSH, Sftunnel, or ICMP response kits. These kits are sent through the application management interface via the internal switchboard to the Internet. 說明 Help 在管理上行鏈路介面上配置交換機捕獲時,僅捕獲從應用管理介面傳送的入口資料包。不會捕獲發往應用程式管理介面的資料包。 When you configure a switchboard capture on the upper line link interface, only the access package sent from the application management interface is captured. The package sent to the application management interface is not captured. 此表格總結列出作業: The summary of this table lists the homework: 工作 捕獲點 內部篩選器 Internal Selector 方向 捕獲的流量 captured traffic 在管理上行鏈路介面上配置並檢驗資料包捕獲 Configure and verify data pack capture on the managed line link interface in_mgmt_uplink1 無 None 僅限入口* Access only* (透過內部交換機從管理介面連線到網路) (from managing interface to network via internal switchboard) 從FTD管理IP位址192.0.2.200到主機192.0.2.100的ICMP回應回覆 From FTD management IP address 192.02.200 to host ICMP response 192.02.100 從FTD管理IP位址192.0.2.200到FMC IP位址192.0.2.101的Sftunnel From FTD management IP address 192.02.200 to FMC IP address 192.02.101 Sftunnel 從FTD管理IP位址192.0.2.200到主機192.0.2.100的SSH From FTD managing IP address 192.02.200 to host 192.02.100 SSH * 與3100不同,安全防火牆4200支援雙向(入口和出口)捕獲。 * Unlike 3100, the security firewall 4200 backstops two-way (entry and exit) captures. 內部交換機資料包捕獲過濾器的配置方式與資料平面捕獲的配置方式相同。使用ethernet-type和match選項配置過濾器。 The internal switch box is configured to capture filters in the same way as the data level. The filters are configured using the options ethnet-type and match. 組態 在ASA或FTD CLI上執行以下步驟,使用與來自主機198.51.100.100的ARP幀或ICMP資料包匹配的過濾器配置資料包捕獲(介面Ethernet1/1): Execute the following steps on ASA or FTD CLI, using filter configuration kits matching ARP or ICMP data packs of 198.51.10.100 for the Autonomous Machine (Ethernet1/1): 驗證 Verify/strong> 驗證捕獲會話名稱和過濾器。以十進位制表示,Ethertype值為2054,十六進位制表示為0x0806: Validate capture session names and filters. In decimals, the Ethertype value is 2054 and the hexadecimal value is 0x0806: 這是對ICMP過濾器的驗證。IP協定1是ICMP: This is an ICMP filter. IP protocol 1 is ICMP: 使用ASA或FTD CLI收集內部交換機捕獲檔案。在FTD上,也可透過CLI的copy命令將擷取檔案匯出到透過資料或診斷介面可存取的目標。 Collects files from internal exchanges using ASA or FTD CLI. On the FTD, you can also export the seized files to the target that is accessible through the data or diagnostic interface via the CLI's copy command. 或者,您可以在專家模式下將檔案複製到/ngfw/var/common中,然後透過File Download選項從FMC中下載該檔案。 Alternatively, you can copy the file in expert mode to /ngfw/var/common and download the file from the FMC through File Download options. 對於埠通道介面,請確保從所有成員介面收集資料包捕獲檔案。 For port interfaces, make sure that files are collected from all members. ASA 按照以下步驟在ASA CLI上收集內部交換機捕獲檔案: Collect internal switchboard capture files on ASA CLI in accordance with the following steps: 使用CLI的copy命令將檔案導出到遠端目標: Using CLI's copy command to direct the file to a remote target: FTD 按照以下步驟收集FTD CLI上的內部交換器擷取檔案,並將其複製到透過資料或診斷介面可存取的伺服器: Collect files from the FTD CLI internal switches and copy them to servers accessible through data or diagnostic interfaces as follows: 按照上的以下步驟透過檔案下載選項從FMC收集捕獲檔案: Download files at the following step: 準則和限制: 在多情景ASA中,交換機在資料介面上的捕獲是在使用者情景中配置的。僅在管理情景中支援交換機在in_data_uplink1和in_mgmt_uplink1介面上捕獲。 這是基於TAC案例中資料包捕獲使用情況的最佳實踐清單: This is the best list of applications based on data pack capture in the TAC case:> show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: enabled
Oper State: up
Oper State Reason: Active
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 2
Physical port:
Slot Id: 1
Port Id: 4
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-4-0.pcap
Pcapsize: 23442
Filter: capsw-1-4
Packet Capture Filter Info
Name: capsw-1-4
Protocol: 0
Ivlan: 0
Ovlan: 205
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Physical port:
Slot Id: 1
Port Id: 3
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-3-0.pcap
Pcapsize: 5600
Filter: capsw-1-3
Packet Capture Filter Info
Name: capsw-1-3
Protocol: 0
Ivlan: 0
Ovlan: 205
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
49 packet captured on disk using switch capture
Reading of capture file from disk is not supported> connect fxos
…
firewall# connect local-mgmt
firewall(local-mgmt)# show portchannel summary
Flags: D - Down P - Up in port-channel (members)
I - Individual H - Hot-standby (LACP only)
s - Suspended r - Module-removed
S - Switched R - Routed
U - Up (port-channel)
M - Not in use. Min-links not met
-------------------------------------------------------------------------------
Group Port- Type Protocol Member Ports
Channel
--------------------------------------------------------------------------------
1 Po1(U) Eth LACP Eth1/3(P) Eth1/4(P)
LACP KeepAlive Timer:
--------------------------------------------------------------------------------
Channel PeerKeepAliveTimerFast
--------------------------------------------------------------------------------
1 Po1(U) False
Cluster LACP Status:
--------------------------------------------------------------------------------
Channel ClusterSpanned ClusterDetach ClusterUnitID ClusterSysID
--------------------------------------------------------------------------------
1 Po1(U) False False 0 clust
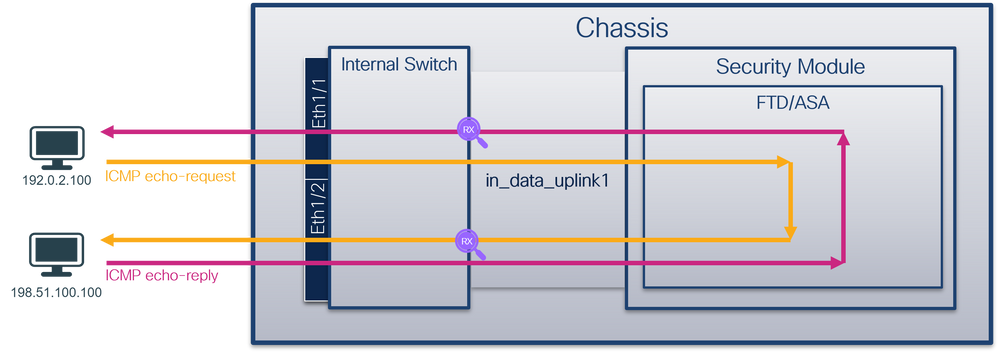
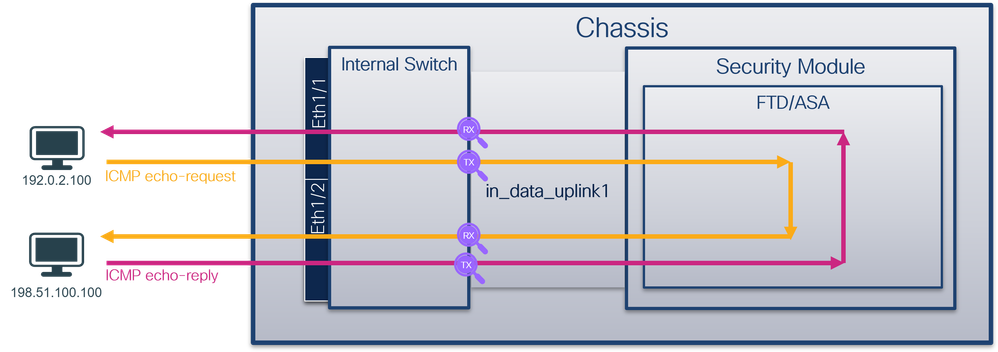
> capture capsw switch interface in_data_uplink1
> capture capsw switch interface in_data_uplink1 direction ?
both To capture switch bi-directional traffic
egress To capture switch egressing traffic
ingress To capture switch ingressing traffic
> capture capsw switch interface in_data_uplink1 direction both> no capture capsw switch stop
> show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: enabled
Oper State: up
Oper State Reason: Active
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 1
Physical port:
Slot Id: 1
Port Id: 18
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-data-uplink1.pcap
Pcapsize: 7704
Filter: capsw-1-18
Packet Capture Filter Info
Name: capsw-1-18
Protocol: 0
Ivlan: 0
Ovlan: 0
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
66 packets captured on disk using switch capture
Reading of capture file from disk is not supported> connect fxos
…
firewall# connect local-mgmt
firewall(local-mgmt)# show portmanager switch status
Dev/Port Mode Link Speed Duplex Loopback Mode Port Manager
--------- ---------------- ----- ----- ------ ------------- ------------
0/1 SGMII Up 1G Full None Link-Up
0/2 SGMII Up 1G Full None Link-Up
0/3 SGMII Up 1G Full None Link-Up
0/4 SGMII Up 1G Full None Link-Up
0/5 SGMII Down 1G Half None Mac-Link-Down
0/6 SGMII Down 1G Half None Mac-Link-Down
0/7 SGMII Down 1G Half None Mac-Link-Down
0/8 SGMII Down 1G Half None Mac-Link-Down
0/9 1000_BaseX Down 1G Full None Link-Down
0/10 1000_BaseX Down 1G Full None Link-Down
0/11 1000_BaseX Down 1G Full None Link-Down
0/12 1000_BaseX Down 1G Full None Link-Down
0/13 1000_BaseX Down 1G Full None Link-Down
0/14 1000_BaseX Down 1G Full None Link-Down
0/15 1000_BaseX Down 1G Full None Link-Down
0/16 1000_BaseX Down 1G Full None Link-Down
0/17 1000_BaseX Up 1G Full None Link-Up
0/18 KR2 Up 50G Full None Link-Up
0/19 KR Up 25G Full None Link-Up
0/20 KR Up 25G Full None Link-Up
0/21 KR4 Down 40G Full None Link-Down
0/22 n/a Down n/a Full N/A Reset
0/23 n/a Down n/a Full N/A Reset
0/24 n/a Down n/a Full N/A Reset
0/25 1000_BaseX Down 1G Full None Link-Down
0/26 n/a Down n/a Full N/A Reset
0/27 n/a Down n/a Full N/A Reset
0/28 n/a Down n/a Full N/A Reset
0/29 1000_BaseX Down 1G Full None Link-Down
0/30 n/a Down n/a Full N/A Reset
0/31 n/a Down n/a Full N/A Reset
0/32 n/a Down n/a Full N/A Reset
0/33 1000_BaseX Down 1G Full None Link-Down
0/34 n/a Down n/a Full N/A Reset
0/35 n/a Down n/a Full N/A Reset
0/36 n/a Down n/a Full N/A Reset 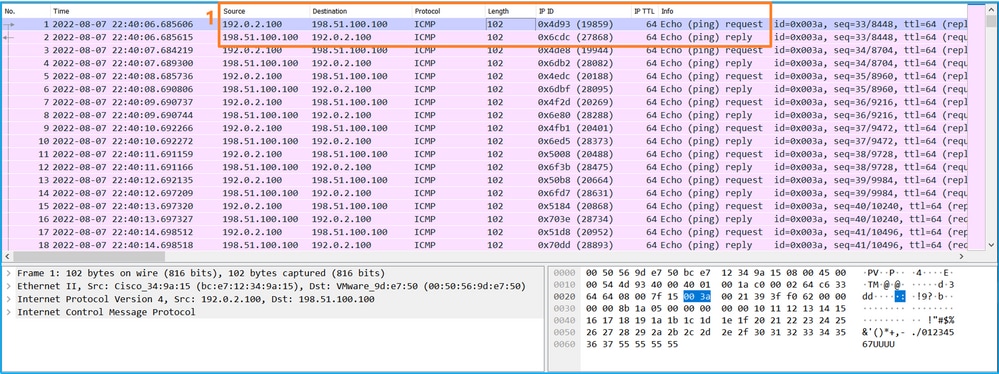
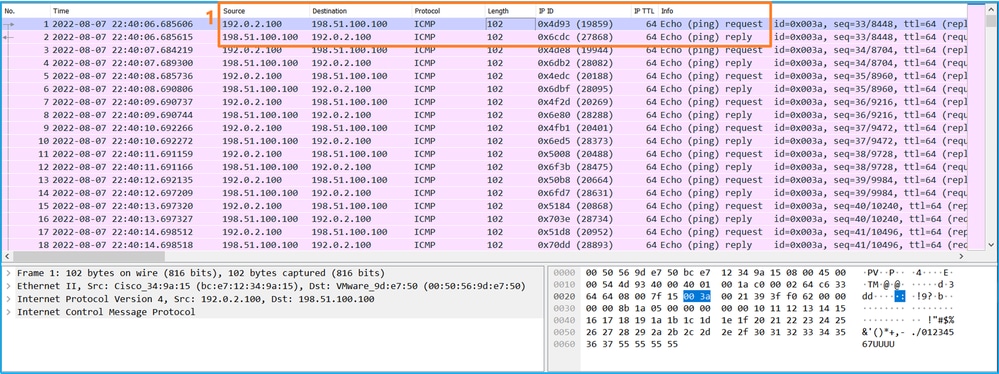
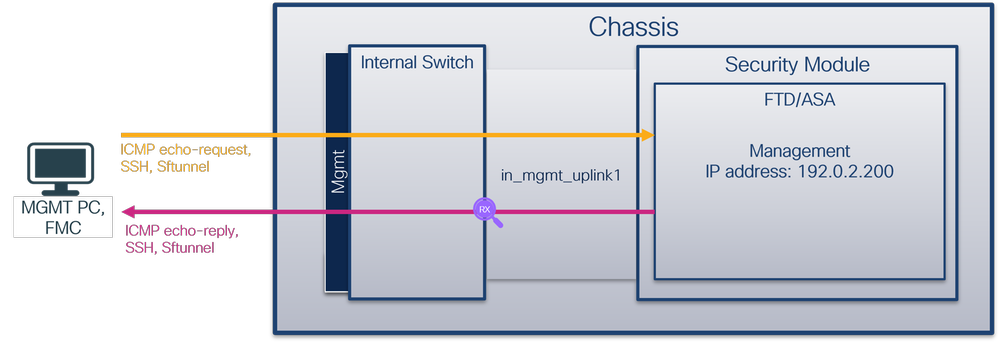
> capture capsw switch interface in_mgmt_uplink1
> capture capsw switch interface in_mgmt_uplink1 direction ?
both To capture switch bi-directional traffic
egress To capture switch egressing traffic
ingress To capture switch ingressing traffic
> capture capsw switch interface in_mgmt_uplink1 direction both> no capture capsw switch stop
> show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: enabled
Oper State: up
Oper State Reason: Active
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 1
Physical port:
Slot Id: 1
Port Id: 19
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-mgmt-uplink1.pcap
Pcapsize: 137248
Filter: capsw-1-19
Packet Capture Filter Info
Name: capsw-1-19
Protocol: 0
Ivlan: 0
Ovlan: 0
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
281 packets captured on disk using switch capture
Reading of capture file from disk is not supported> connect fxos
…
firewall# connect local-mgmt
firewall(local-mgmt)# show portmanager switch status
Dev/Port Mode Link Speed Duplex Loopback Mode Port Manager
--------- ---------------- ----- ----- ------ ------------- ------------
0/1 SGMII Up 1G Full None Link-Up
0/2 SGMII Up 1G Full None Link-Up
0/3 SGMII Up 1G Full None Link-Up
0/4 SGMII Up 1G Full None Link-Up
0/5 SGMII Down 1G Half None Mac-Link-Down
0/6 SGMII Down 1G Half None Mac-Link-Down
0/7 SGMII Down 1G Half None Mac-Link-Down
0/8 SGMII Down 1G Half None Mac-Link-Down
0/9 1000_BaseX Down 1G Full None Link-Down
0/10 1000_BaseX Down 1G Full None Link-Down
0/11 1000_BaseX Down 1G Full None Link-Down
0/12 1000_BaseX Down 1G Full None Link-Down
0/13 1000_BaseX Down 1G Full None Link-Down
0/14 1000_BaseX Down 1G Full None Link-Down
0/15 1000_BaseX Down 1G Full None Link-Down
0/16 1000_BaseX Down 1G Full None Link-Down
0/17 1000_BaseX Up 1G Full None Link-Up
0/18 KR2 Up 50G Full None Link-Up
0/19 KR Up 25G Full None Link-Up
0/20 KR Up 25G Full None Link-Up
0/21 KR4 Down 40G Full None Link-Down
0/22 n/a Down n/a Full N/A Reset
0/23 n/a Down n/a Full N/A Reset
0/24 n/a Down n/a Full N/A Reset
0/25 1000_BaseX Down 1G Full None Link-Down
0/26 n/a Down n/a Full N/A Reset
0/27 n/a Down n/a Full N/A Reset
0/28 n/a Down n/a Full N/A Reset
0/29 1000_BaseX Down 1G Full None Link-Down
0/30 n/a Down n/a Full N/A Reset
0/31 n/a Down n/a Full N/A Reset
0/32 n/a Down n/a Full N/A Reset
0/33 1000_BaseX Down 1G Full None Link-Down
0/34 n/a Down n/a Full N/A Reset
0/35 n/a Down n/a Full N/A Reset
0/36 n/a Down n/a Full N/A Reset 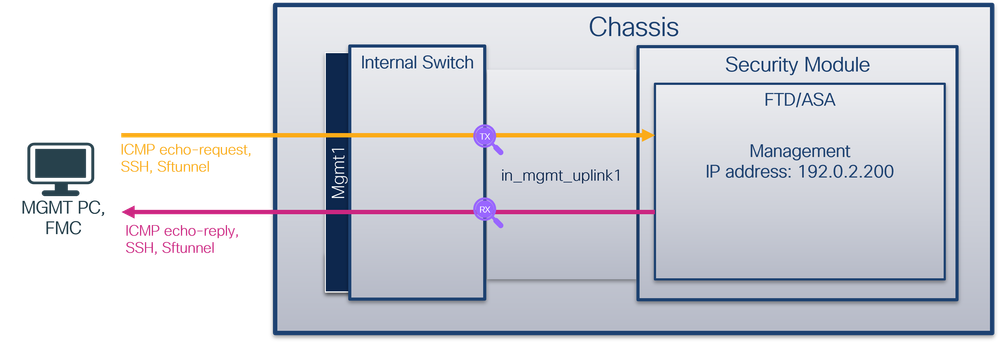

> show nameif
Interface Name Security
Ethernet1/1 inside 0
Ethernet1/2 outside 0
Management1/1 diagnostic 0
> capture capsw switch interface inside ethernet-type arp
> capture capsw switch interface inside match icmp 198.51.100.100
> show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: disabled
Oper State: down
Oper State Reason: Session_Admin_Shut
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 1
Physical port:
Slot Id: 1
Port Id: 1
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap
Pcapsize: 0
Filter: capsw-1-1
Packet Capture Filter Info
Name: capsw-1-1
Protocol: 0
Ivlan: 0
Ovlan: 0
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 2054
Total Physical breakout ports involved in Packet Capture: 0
0 packet captured on disk using switch capture
Reading of capture file from disk is not supported> show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: disabled
Oper State: down
Oper State Reason: Session_Admin_Shut
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 1
Physical port:
Slot Id: 1
Port Id: 1
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap
Pcapsize: 0
Filter: capsw-1-1
Packet Capture Filter Info
Name: capsw-1-1
Protocol: 1
Ivlan: 0
Ovlan: 0
Src Ip: 198.51.100.100
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
0 packets captured on disk using switch capture
Reading of capture file from disk is not supported
asa# capture capsw switch stop
asa# show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: disabled
Oper State: down
Oper State Reason: Session_Admin_Shut
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 1
Physical port:
Slot Id: 1
Port Id: 1
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap
Pcapsize: 139826
Filter: capsw-1-1
Packet Capture Filter Info
Name: capsw-1-1
Protocol: 0
Ivlan: 0
Ovlan: 0
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
886 packets captured on disk using switch capture
Reading of capture file from disk is not supported
asa# copy flash:/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap ?
cluster: Copy to cluster: file system
disk0: Copy to disk0: file system
disk1: Copy to disk1: file system
flash: Copy to flash: file system
ftp: Copy to ftp: file system
running-config Update (merge with) current system configuration
scp: Copy to scp: file system
smb: Copy to smb: file system
startup-config Copy to startup configuration
system: Copy to system: file system
tftp: Copy to tftp: file system
asa# copy flash:/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap tftp://198.51.100.10/
Source filename [/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap]?
Destination filename [sess-1-capsw-ethernet-1-1-0.pcap]?
Copy in progress...C
139826 bytes copied in 0.532 secs
> system support diagnostic-cli
Attaching to Diagnostic CLI ... Click 'Ctrl+a then d' to detach.
Type help or '?' for a list of available commands.
firepower> enable
Password: <-- Enter
firepower#
firepower# capture capi switch stop
firepower# show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: disabled
Oper State: down
Oper State Reason: Session_Admin_Shut
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 1
Physical port:
Slot Id: 1
Port Id: 1
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap
Pcapsize: 139826
Filter: capsw-1-1
Packet Capture Filter Info
Name: capsw-1-1
Protocol: 0
Ivlan: 0
Ovlan: 0
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
886 packets captured on disk using switch capture
Reading of capture file from disk is not supported
firepower# copy flash:/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap ?
cluster: Copy to cluster: file system
disk0: Copy to disk0: file system
disk1: Copy to disk1: file system
flash: Copy to flash: file system
ftp: Copy to ftp: file system
running-config Update (merge with) current system configuration
scp: Copy to scp: file system
smb: Copy to smb: file system
startup-config Copy to startup configuration
system: Copy to system: file system
tftp: Copy to tftp: file system
firepower# copy flash:/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap tftp://198.51.100.10/
Source filename [/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap]?
Destination filename [sess-1-capsw-ethernet-1-1-0.pcap]?
Copy in progress...C
139826 bytes copied in 0.532 secs
> capture capsw switch stop
> show capture capsw detail
Packet Capture info
Name: capsw
Session: 1
Admin State: disabled
Oper State: down
Oper State Reason: Session_Admin_Shut
Config Success: yes
Config Fail Reason:
Append Flag: overwrite
Session Mem Usage: 256
Session Pcap Snap Len: 1518
Error Code: 0
Drop Count: 0
Total Physical ports involved in Packet Capture: 1
Physical port:
Slot Id: 1
Port Id: 1
Pcapfile: /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap
Pcapsize: 139826
Filter: capsw-1-1
Packet Capture Filter Info
Name: capsw-1-1
Protocol: 0
Ivlan: 0
Ovlan: 0
Src Ip: 0.0.0.0
Dest Ip: 0.0.0.0
Src Ipv6: ::
Dest Ipv6: ::
Src MAC: 00:00:00:00:00:00
Dest MAC: 00:00:00:00:00:00
Src Port: 0
Dest Port: 0
Ethertype: 0
Total Physical breakout ports involved in Packet Capture: 0
886 packets captured on disk using switch capture
Reading of capture file from disk is not supported
> expert
admin@firepower:~$ sudo su
root@firepower:/home/admin
root@KSEC-FPR3100-1:/home/admin cp /mnt/disk0/packet-capture/sess-1-capsw-ethernet-1-1-0.pcap /ngfw/var/common/
root@KSEC-FPR3100-1:/home/admin ls -l /ngfw/var/common/sess*
-rwxr-xr-x 1 root admin 139826 Aug 7 20:14 /ngfw/var/common/sess-1-capsw-ethernet-1-1-0.pcap
-rwxr-xr-x 1 root admin 24 Aug 6 21:58 /ngfw/var/common/sess-1-capsw-ethernet-1-3-0.pcap
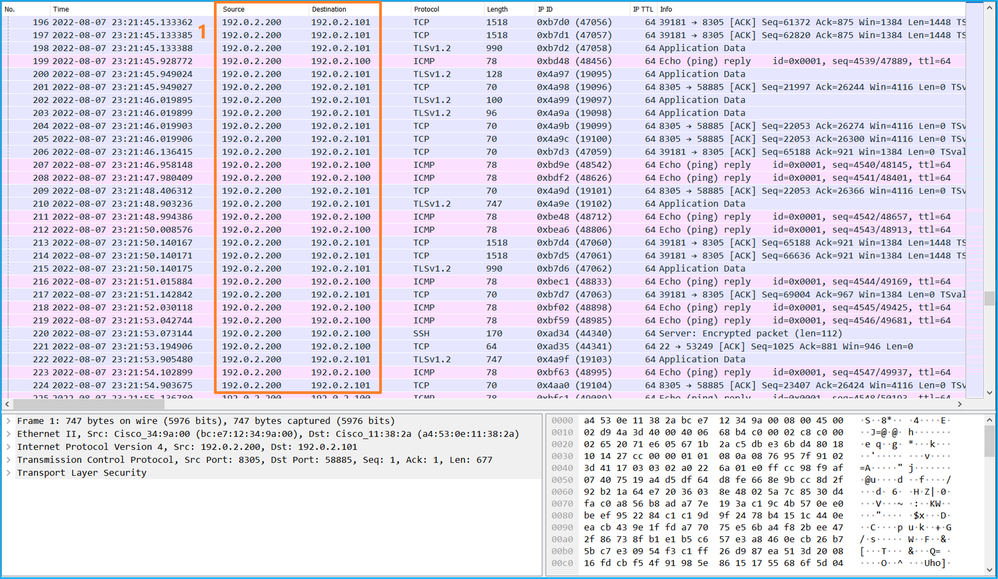
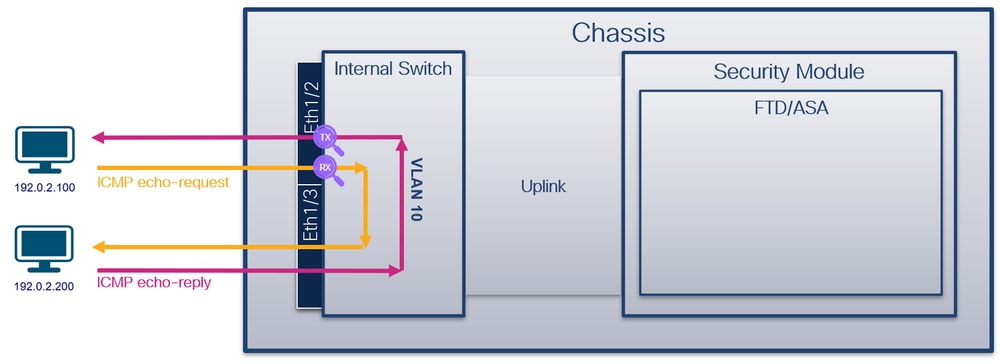
注册有任何问题请添加 微信:MVIP619 拉你进入群

打开微信扫一扫
添加客服
进入交流群




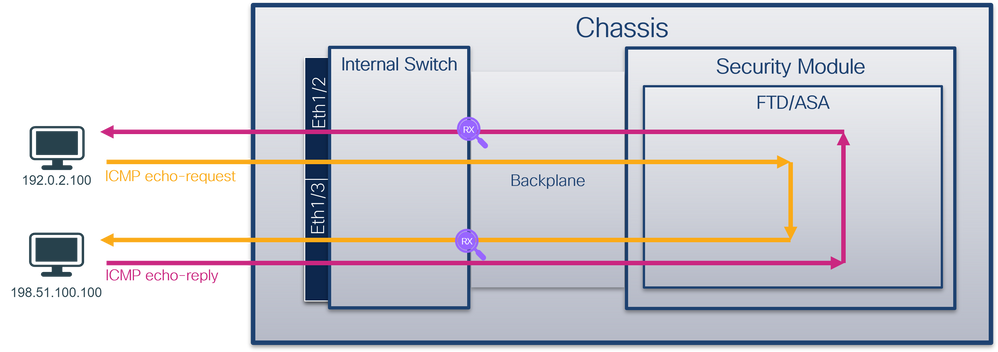
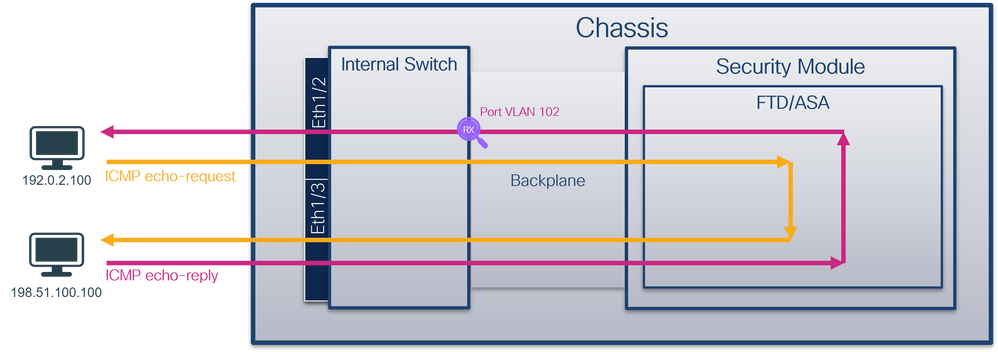
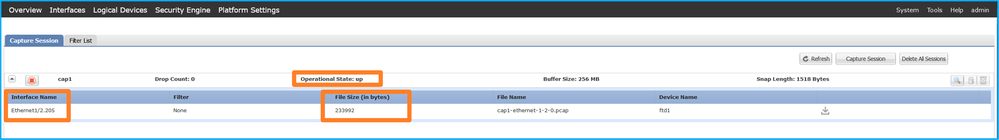
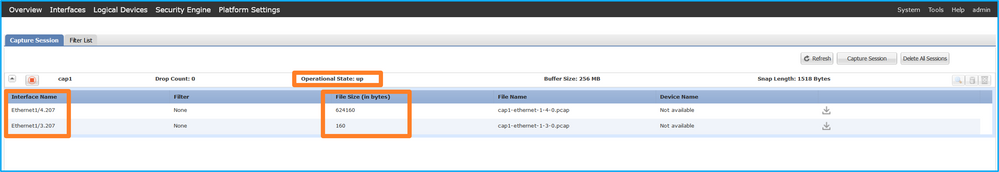
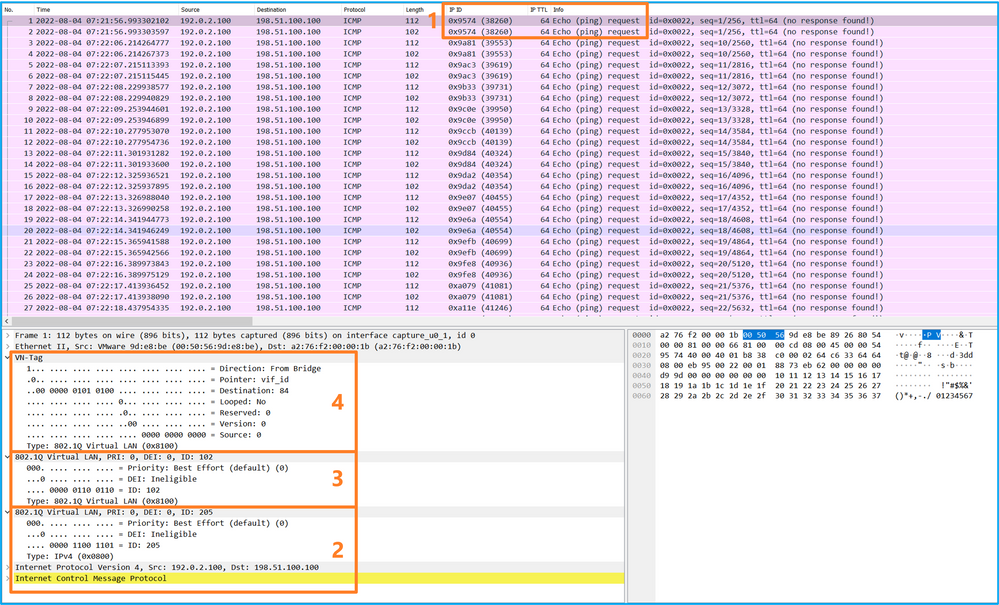
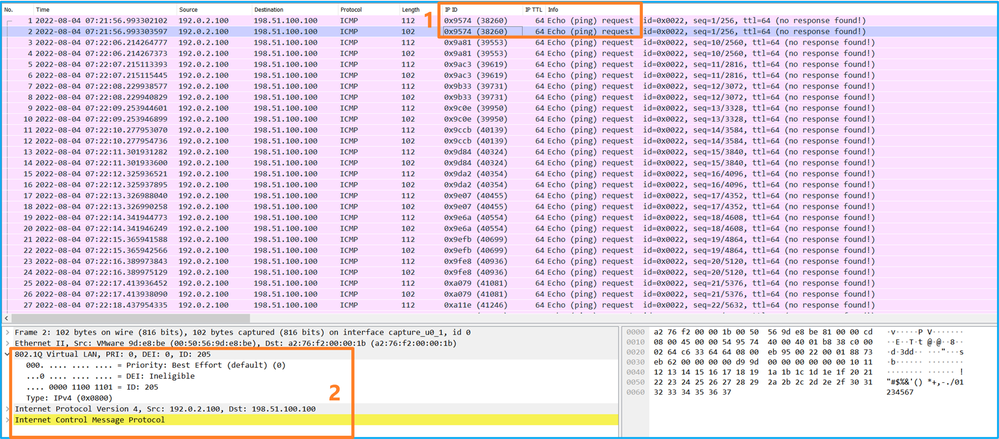
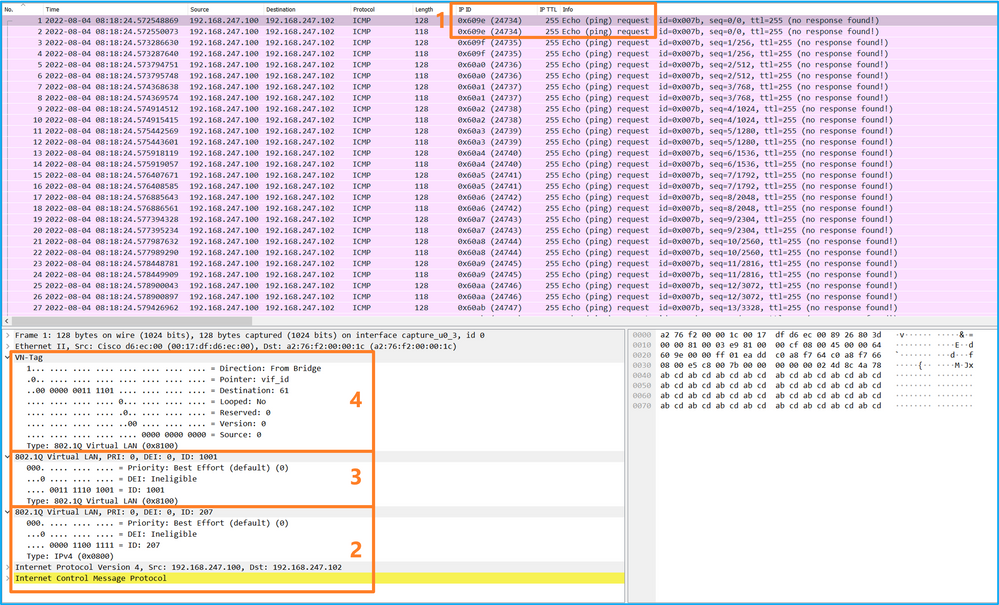
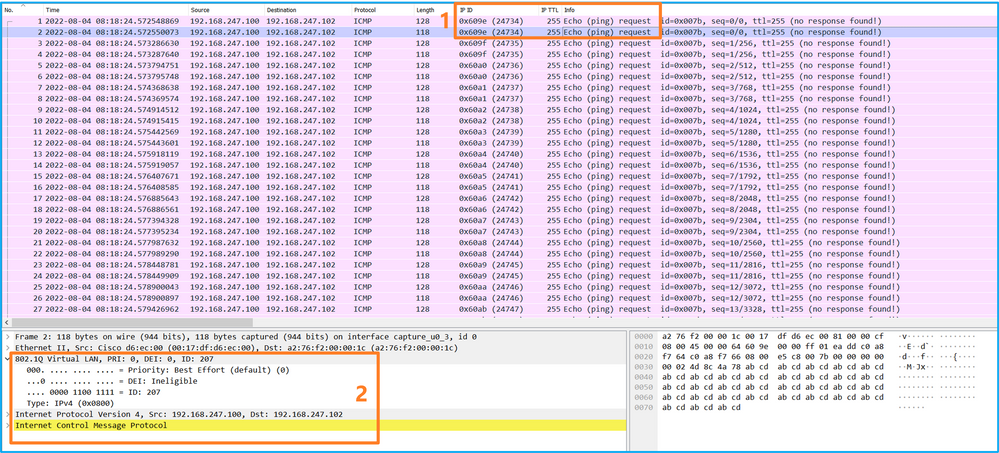












发表评论